Researchers have discovered a new Mac malware which encrypts files like a piece of ransomware on compromised systems, but also allows its operators to steal data and take full control of an infected computer.
The malware was initially called EvilQuest and was later renamed ThiefQuest to prevent confusion as EvilQuest is the name of a video game. When the malware was first identified, the samples were not detected by any of the antivirus engines on VirusTotal, but more than a dozen engines detect it at the time of writing.
Malwarebytes has seen the malware distributed as trojanized installers for popular macOS applications, including the Little Snitch firewall, the Mixed In Key and Ableton DJ apps, and an update to Google software.
Patrick Wardle, a researcher specializing in Apple’s security products, pointed out that because these installers are not signed, macOS warns users before opening them, but people downloading pirated software are likely to disregard the warning and install the malware on their computer.
Wardle has provided a comprehensive review of how ThiefQuest is built, how longevity is achieved and how its capabilities are achieved. It starts encrypting certain types of files found on the system once the malware has been deployed, including archives, images , audio and video files , documents, spreadsheets, presentations, databases and web files.
It then drops a text file that warns users that their files have been compromised and instructs them to pay $50 in bitcoin for their recovery. In a modal window a description of the ransom note is also shown, and its content is read out using the speech function in macOS.
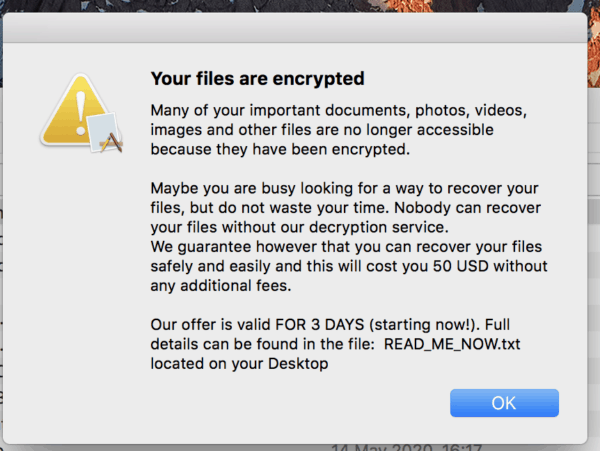
In addition to the ransomware functionality, Wardle says, ThiefQuest may scan and exfiltrate files that may contain useful information, such as wallet data from cryptocurrencies, and trigger a keylogger. The intruder can also instruct the malware to execute commands remotely, and may use it to create a reverse shell. Basically, an intruder might use those capabilities to take full control of a computer, Wardle cautioned.
Researchers at malwarebytes state that they have yet to decide whether ThiefQuest encrypted files can be retrieved. An analysis conducted by Bleeping Computer, however, suggests that ThiefQuest could actually be a wiper disguised as ransomware, since users may not be able to recover their files even if they pay the ransom. The aim could be to use the tactics of ransomware to hide the other malicious activities.
Bleeping Computer has found out that the same Bitcoin address for paying the ransom is given to all victims, and the ransom note does not contain an email address or other information for contacting the attacker. The perpetrator is unable to say who paid the ransom and victims cannot contact them to request the decryption device until they pay up.
The ransom note says decryption would start automatically within two hours of making the payment, but this is unlikely to occur given how the malware was built. Throughout the time of writing, no transactions were made with the bitcoin address in the ransom note.











Leave a Reply