There may be vulnerability in Trend Micro’s Password Manager to run programs which have the most privileged Windows account permissions.
An attacker already in the computer could use the vulnerability to execute an arbitrary, unsigned DLL file with SYSTEM privileges in a trusted process.
An adversary would benefit because he could carry out malicious payloads and escape detection.
The Trend Micro Password Management Tool is available as standalone software and includes Premium and Maximum Security 2019 antivirus versions for consumers.
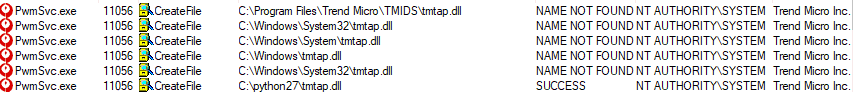
The weakness was due to the “Trend Micro Password Manager Central Control Service” (PwmSvc.exe), which begins a chain reaction involving looking for a DLL not present on the system (tmtap.dll).
System folders and a c:/python27 search locations for the absent file allow for exploitation.
“As you can see, the service was trying to load a missing DLL file, which eventually was loaded from the c:\python27 directory – a directory within our PATH environment variable,” Hadar says.
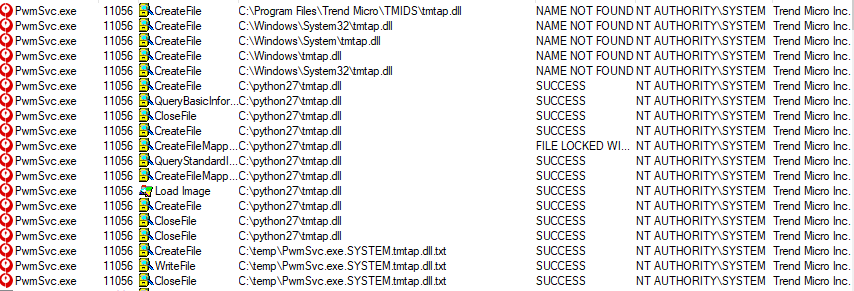
Hadar compiled an unsigned DLL to test the privilege scales that wrote to a text file the name of the loading process, the username and the name of the DLL file.
As illustrated in the following picture, the trial was a success, as the DLL conducted a trusted trend micro process with SYSTEM privileges.
This would also ensure that the malicious executable file remains on a system that has a vulnerable Trend Micro Password Manager version. This would happen because each time the PwmSvc.exe service loads would execute the payload.
The vulnerability (CVE-2019-14684) was identified by the security researcher due to a lack of mechanisms to check that loaded binaries are signed and loaded from a controlled path.
In the same application, Trend Micro received a report with a similar DLL hijacking defect, identified as CVE-2019-14687.
Tr Sen Văn Khang of the Infiniti Team-VinCSS discovered this second bug, and operation included a different DLL, antivirus manufacturer reports in a consulting document.
Trend Micro’s password manager supports automated updates and the patch should already be received by users who have the feature enabled. If this is not the case, the trick should be done manually.











Leave a Reply