A DoS attack, also known as a Denial of Service attack, is a method of affecting a computer system by flooding it with traffic from multiple sources. This can be done for the purpose of disrupting normal operations or even forcing the system to shut down. In this article, we will explore what a DoS attack is and how you can protect yourself from them. We will also provide tips on how to identify and prevent them from happening in the first place.
What is a ddos attack?
A denial-of-service attack is a type of cyberattack that uses resources of a target computer network to deny legitimate users access to the system. The attacker targets multiple systems simultaneously, making it difficult for the target users to access essential services.
The Different Types of Ddos Attacks
A denial of service (DOS) attack is an attempt to prevent a computer system or network from functioning by overloading it with requests. DOS attacks are often used to bring a system down by swamping it with traffic, preventing authorized users from accessing resources or performing their jobs.
DoS attacks can be carried out in many different ways, but all work the same basic way: the attacker sends a flood of traffic to the victim, hoping that some will get stuck and cause the machine to crash. Different types of DoS attacks use different techniques to achieve their goals, but they all share one goal: to stop the target from functioning.
There are several common types of DoS attacks. SYN floods are simply waves of Requests for Service (RFS) that crash systems because they pile up and overload the network interface.
UDP floods send packets indiscriminately and rely on coincidence rather than planning to overwhelm systems; however, UDP-based DDoS attacks have become more popular in recent years because they are harder to detect and defend against than traditional ICMP floods.
IP spoofing attacks involve pretending to be part of a different network address than you are; this ability allows attackers to bypass firewalls and other protection mechanisms by sending malicious traffic through vulnerable servers or networks.
And finally, DNS reflection attacks abuse the Domain Name System (DNS) by tricking victims into thinking requests for specific domains are coming from their own machines.
How to protect yourself from a ddos attack?
A denial-of-service attack is an attempt to make a machine or network resource unavailable to its intended users. A hacker might use a ddos attack to make a website or online service unavailable to its users, for example by flooding it with traffic so that it crashes.
How Do DDoS Attacks Work?
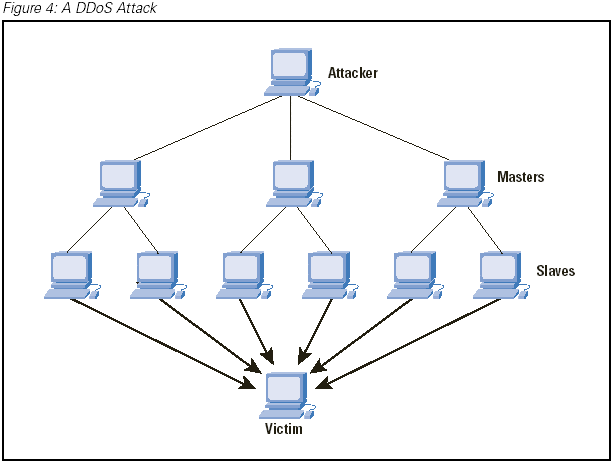
A distributed denial-of-service (DDoS) attack is a type of cyberattack in which multiple machines are used to send traffic to a website or online service so as to overload it and cause it to crash or become unavailable. DDoS attacks are often used as a form of cyberterrorism, by using them against websites or services whose owners the attacker disagrees with. They can also be used for extortion, to cause financial losses from a company’s customers, or simply for disruptive purposes. The most common way attackers launch DDoS attacks is by flooding a target’s computer with fake requests for web pages from different IP addresses. These requests flood the target’s server and slow down or completely stop the victim’s access to the internet.
Who Are the Victims of a DDoS Attack?
A distributed denial of service attack, or ddos attack, is a type of cyberattack in which a perpetrator causes systems or networks to become overloaded by sending malicious requests to them. This can be done by using a large number of systems simultaneously or by exploiting vulnerabilities in software. The goal of a ddos attack is to make a website or system unavailable to its users.
What Can We Do to Protect Ourselves from a DDoS Attack?
DDoS attacks are a form of cyberattack in which multiple devices (computer systems, servers, routers, and so on) are used to send traffic to a target over a period of time with the goal of overwhelming its resources and causing it to fail. DDoS attacks can be carried out using a variety of methods, including flooding (sending large amounts of data to a target), spoofing (using fake IP addresses to disguise the origin of the attack), and Larson-Tomlinson syndrome (a type of amplification attack in which attackers send malicious requests that trigger responses from legitimate servers).
There is no one definitive way to prevent or mitigate against a ddos attack, as each situation is unique. But there are certain steps you can take to protect yourself from potential threats:
- Educate yourself about ddos attacks and how they work. By understanding the basics of ddos attacks, you can better identify potential threats and make informed decisions when protecting your online security.
- Use precautionary measures when online. Keep your computer protected by using anti-virus software and firewall protection, ensure your browser is up-to-date, and avoid clicking on links you don’t trust.
- Remain aware of the latest cybersecurity news and updates. Stay up-to-date on the latest developments in ransomware, DDoS attacks, and other online threats by subscribing to industry newsletters or following relevant blogs or social media accounts.
- Maintain a strong cyber hygiene policy. Follow standard best practices for online security, such as not clicking on links in unsolicited emails, and never sharing your login information or other sensitive information online.
- Report any suspicious activity or threats to your cyber security provider. If you experience a problem with your computer or online account, don’t panic – first try to solve the issue yourself before reporting it to a cyber security provider. But if you can’t solve the problem and believe that your account has been compromised, it is important to report the matter immediately.
How to Respond to a DDoS Attack?
When a website or online service is subjected to a distributed denial-of-service attack (DDoS), the attackers flood the targeted site with traffic in an effort to make it unavailable to legitimate users. DDoS attacks can come in many forms, but all share one common goal: making a site inaccessible so that its owners cannot earn income from it.
There are many ways to respond to a DDoS attack. You can try to mitigate the damage by reducing your site’s bandwidth usage, upgrading your security measures, or contacting the hosting provider and asking for help. However, these actions may not be enough if your site is especially vulnerable to DDoS attacks. In those cases, you may need to take action on behalf of your site’s users.
One way you can protect your users from DDoS attacks is by using a content delivery network (CDN). A CDN helps distribute web pages around the globe so that they load more quickly and without placing an undue load on servers in specific countries or regions. This makes it much harder for attackers who are seeking to disrupt websites by flooding them with traffic.
If you experience regular DDoS attacks, consider beefing up your website’s security measures by using anti-virus software and firewalls, installing intrusion detection systems (IDS), and adding additional layers of security such as two factor authentication (2FA). In some cases, you may also need to contact law enforcement authorities if your website is being used for illegal activities.
Conclusion
A denial of service attack (DoS) is when a hacker sends malicious traffic over the internet in an attempt to prevent someone from using their computer, website, or network. This can be done by flooding a server with requests so that it cannot handle legitimate requests and becomes overloaded, crashing the server or shutting it down altogether. A ddos attack is very harmful because not only does it shut down an entire business or organization, but it also compromises the security of people who are using that site. If you’re ever unsure if something is a ddos attack, don’t hesitate to contact your internet provider for more information.










FIND US ON SOCIALS