For an exploit chain, Amazon has awarded a $18,000 bug bounty that may have allowed an attacker to take full possession of a Kindle e-reader simply by knowing the email address of the intended customer.
Yogev Bar-On, a researcher at the Israel-based cybersecurity consultancy company Realmode Laboratories, discovered the threat, called KindleDrip, in October 2020. KindleDrip included three separate vulnerability vulnerabilities being abused, all of which were resolved by Amazon.
The first exploit chain flaw was linked to the “Send to Kindle” feature, which allows users to send as an attachment an e-book in MOBI format to their Kindle computer via email. Amazon creates an email address @kindle.com where a user can send e-books from a list of email addresses accepted by the user as an attachment.
Bar-On noticed that in order to submit a specially designed e-book that would allow him to execute arbitrary code on the targeted computer, he could exploit this function. By exploiting a flaw relating to a library used by the Kindle to parse JPEG XR files, the malicious e-book achieved code execution. Exploitation allowed the user to click on a connection that included a malicious JPEG XR image within an e-book, which would open a web browser and run the attacker’s code with restricted privileges.
The researcher also found a loophole that allowed him to increase privileges and run the root code, allowing him full access to the system.
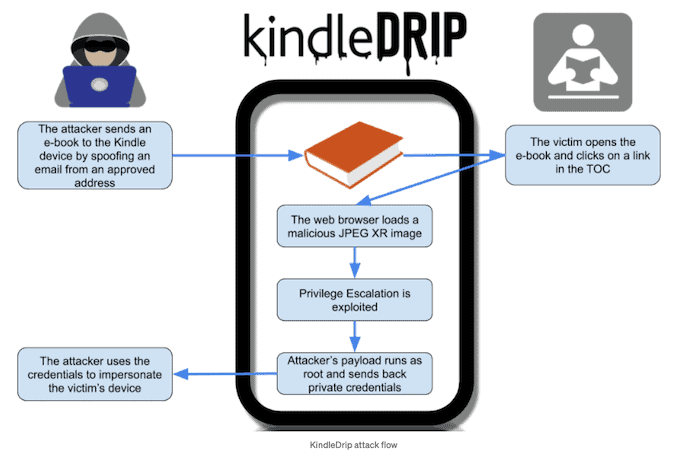
The intruder was able to obtain computer passwords and make transactions using the victim’s credit card at the Kindle store. In a blog post, Bar-On clarified that attackers could sell an e-book at the store and pass cash to their account. The confirmation email will at least make the victim aware of the transaction.’
An attacker will only require the email address of the intended user and to induce the victim to click on a connection inside the malicious e-book. While the Send to Kindle function only encourages users to send e-books from pre-approved email addresses, the investigator found out that an intruder may simply have used an email spoofing service. In certain instances, the intended user’s @kindle.com email address prefix is the same as their daily email.
In December, with the introduction of version 5.13.4, the vulnerability vulnerabilities that demanded improvements to the Kindle firmware — code execution and privilege escalation problems — were fixed. Amazon now also provides email addresses with an authentication connection that can not be authenticated. There is no need for Kindle users to take any action.
To explain how a KindleDrip attack worked, a video was published:











Leave a Reply