Biometric authentication is a security system that more and more companies, businesses, websites, apps, and software use. It makes authentication methods more robust and accurate because it uses people’s unique identifiers by their physical traits.
The most used are fingerprint authentication and face recognition. Until recently, we see finger vein authentication technology become a staple in banking systems and ATMs. The authentication accuracy is the highest compared to other biometric technologies.
Let us take a closer look at these biometric authentication systems to understand how or why they can be breached.
Types of Biometric Authentication Systems:
Facial Recognition System

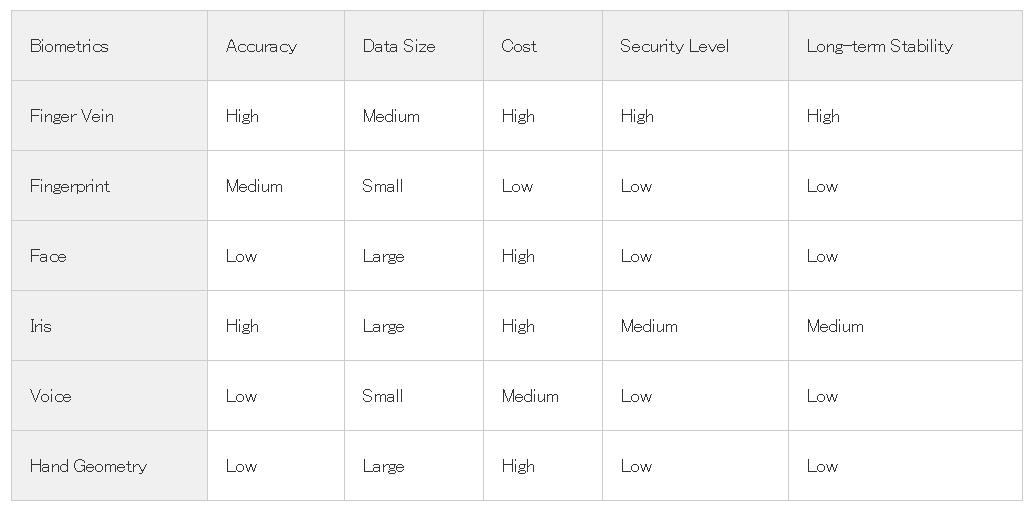
A facial recognition system, also known as Biometric Artificial Intelligence, identifies a human face by mapping facial features in photos, video, or in real-time.
This authentication technology uses algorithms to identify unique, distinctive information about a person’s face, translated into a mathematical model, and linked to data gathered from a face-recognition database.
The data on a specific face is also considered a face prototype and is different from a photograph since it is intended to contain only those features that can be used to differentiate one face from another. It compares details to a database to find a match.
All facial recognition systems are programmed to measure possible match scores between the unknown person and facial templates stored in the database instead of directly identifying the unknown person.
Instead of getting a single result, facial recognition systems would deliver multiple possible matches, ranked in order of possible matching.
Face recognition systems differ in their ability to recognize individuals under challenging environments such as inadequate lighting, low-quality image clarity, and suboptimal viewing angle (like a snapshot taken from a CCTV camera above an unidentified individual).
Despite privacy issues around facial recognition technology, it is more popular than ever and is expected to be a $7.7 billion industry in 2022. It can be used commercially, from law enforcement agencies, surveillance, even marketing.
However, face recognition can be prone to error, which can implicate people for crimes they have not committed. It can give a “false negative” or a “false positive” result.
You cannot rely on facial recognition alone as an authentication method. You need to use other authentication technologies to arrive at the most accurate data possible. It also shows that this technology needs to be used responsibly because it can be abused or misused.
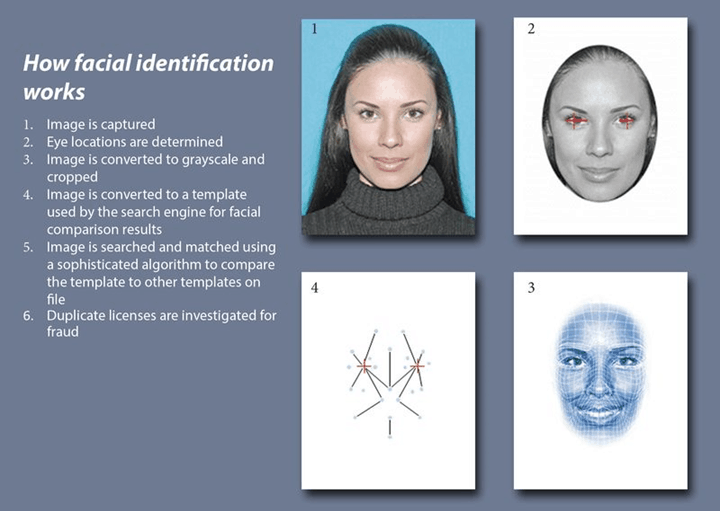
Iris Recognition
Iris recognition is an automatic biometric detection system for taking a high-contrast photograph of a person’s iris using visible and near-infrared light. It may be the irises of an individual’s eyes of one or both, whose intricate shapes are peculiar, stable, and can be seen from a distance.
It is a type of biometric technology in the same category as fingerprinting and facial recognition, but different to retinal scanning, which uses the unique patterns on a person’s retina blood vessels.
Digital models produced by algorithms from these patterns will identify a person or someone claiming to be that person.
Enrolled template databases are measured in millions of templates per second per (single-core) CPU on matcher engines. The false match rate is surprisingly very low.

Advocates of iris scanning technology say it helps law enforcement agents match photographs of a suspect’s iris to an existing image archive to validate a suspect’s identity.
Iris scans are quicker and more precise than fingerprint scans since it’s easier for a person to tweak their fingerprints for scanning than altering their eyes.
Fingerprint Identification

Fingerprint recognition enables identity verification through examining and comparing their dermal finger ridges. This biometric authentication method is the first to be used commercially and is still one of the most common biometric verification today.
With the number of video surveillance cameras increasing in major cities, using data collected by CCTV and surveillance cameras has caused a lot of debate regarding privacy and human rights. Having fingerprint authentication as an additional source of verification can be helpful to ease these concerns.
This biometric technology has one of the longest track records, too, since fingerprint identification has been used for more than a century. It is now automated due to advancements in computing capabilities and is used by law enforcement services and immigration offices and other establishments worldwide.
The foundation for fingerprint identification is the “Galton Points,” named after Sir Francis Galton, of the late nineteenth century. The Galton Points define identifying points or characteristics from which fingerprints can be identified.
This biometric verification can be identified through various sensors like optical, ultrasound, thermal, and capacitive. The most common of these are optical sensors. All these types of sensors collect the digital image of a fingerprint surface.
Fingerprint matching techniques can be minutiae-based matching (exact comparison of ridges and splits) and pattern matching (comparing two images for similarity).
Speech Recognition

Speech recognition is a machines’ ability to respond to spoken commands. Speech recognition facilitates hands-free use of multiple instruments and machinery and provides automated translation, and generates print-ready dictation.
It is frequently used for dictation, querying databases, and computer-based programs, particularly in specialized vocabulary careers. It also allows personal vehicles and mobile assistants like Apple’s Siri and Amazon’s Alexa.
The speech recognition technology is also called Automatic Speech Recognition (ASR), Speech to Text (STT), or computer speech recognition.
Some speech recognition devices require “training” where a speaker reads text or vocabulary within the device. The system analyzes the person’s distinctive voice and uses it to fine-tune the person’s tone, resulting in increased precision.
Training programs are considered “speaker-dependent.” Systems that do not use instruction are referred to as “speaker-independent” systems.
This biometric technology has gone through different innovations. Most recently, development in deep learning and big data have helped speech recognition advance further.
Microsoft gives this simple guide on how to use voice recognition in Windows 10:
- Start by setting up a microphone.
- Ensure you have a microphone set up before you set up voice recognition,
- Select the Start button, then select Settings > Time & Language > Speech.
- Go to Microphone > select the Get Started button.
To train Windows 10 to recognize your voice, you can do the following steps:
- Start by setting up a microphone.
- You can input Windows Speech Recognition in the search box on the taskbar > choose Windows Speech Recognition.
- You will find a dialog box that says, “Welcome to Speech Recognition Voice Training.”
- If you don’t see this dialog box, then type “Control Panel” in the search box on the taskbar > select Control Panel > choose Ease of Access > Speech Recognition > Train your computer to understand you better.
The speech recognition technology has its pros and cons, just like other biometric authentication methods. For instance, while this biometric technology is convenient, it still needs more improvement.
But the advantages outweigh whatever disadvantages there may be, so speech recognition software is becoming more and more popular among consumers.
It is more of a staple in computers and mobile devices for convenience and easy access. However, it still has limitations in precisely capturing words when there are changes in pronunciation.
More translations and improved support also need to be developed for most languages outside of English. Developers should also improve removing background noise as this could lead to inaccuracies.
Finger Vein Recognition

Blood vessel patterns are unique to everyone, as are other biometric data such as fingerprints or the iris’s patterns. Unlike other biometric devices, blood vessel patterns are almost impossible to counterfeit since they are situated under the surface of the skin.
A dummy finger equipped with a copied fingerprint can fool biometric systems; recordings and high-resolution images can fool voice and facial characteristic-based systems. It is also harder to fool the finger vein ID device, since it can only authenticate the finger of a living human.
Finger vein recognition is a method that identifies an individual using the vein pattern inside one’s fingers. With near-infrared light-emitting diode (LED) light and a monochrome charge-coupled device (CCD) camera, the hemoglobin in the blood absorbs near-infrared LED light making the vein system appear like dark line-patterns.
The camera records the image, digitizing, certifying and submitting raw data to a recorded image database. Finger vein ID compares the vascular pattern in an individual’s finger to data previously collected.
In 2005, Hitachi developed and patented a finger vein ID system. Currently, the technology is being used or developed for numerous purposes, including credit card authentication, vehicle security, employee and attendance monitoring, device and network authentication, endpoint security, and automated teller machines.
Keystroke Dynamics

Keystroke dynamics are patterns of timing and rhythm produced when an individual types on a keyboard. It includes overall speed, variations of movement and speed between specific keys, common errors, and duration that keys are pressed.
A type print is the unique keystroke dynamics of a person. Typeprint analysis can be utilized as a password hardening factor or for 2FA, or two-factor authentication.
Keystroke dynamics is a biometric behavioral. This means that ‘you doing something’ is the biometric factor.
The key issue with login-based authentication systems is that after login access has been granted it can not authenticate users.
Risks in Biometric Authentication

Privacy Issues
Biometric authentication poses multiple risks. The most significant risk is the danger of a centralized database that may identify people anonymously, remotely, or in motion, without their approval or consent. It poses serious civil rights and privacy concerns as iris data is taken from more people.
Law enforcement officers may use long-range iris detectors on people who, after being pulled over, simply glance at their rearview mirror. An individual may be identified anywhere, even though they are not suspected of committing a crime.
Biometric data related to people’s whereabouts and their private activities could be leaked, misused, or exploited. If DNA scans became popular, a whole new field of privacy issues might emerge, including exposure to medical problems and family relationships.
Data Security
And then, there are data protection concerns. Is biometric data handled responsibly? Are security measures in place in all these establishments collecting biometric information?
Data leaks are at an all-time peak. If encrypted biometric information is lost or corrupted, it can not be withdrawn, canceled, or reissued.
Growing the possibility of data loss, law enforcement agencies and other establishments often get third-party support to store big data on cloud storage. It leaves another risk as these businesses can gain insight and leverage over social justice records and the like, which several workers can view remotely.
Authentication credentials may leak from computers, company servers, or applications used to examine them, such as fingerprint scans or voice recordings.
False positives and false negatives also pose significant risks. Faces and voices may vary, or recognition mechanisms may be fooled with masks, images and voice samples, fingerprint copies, or manipulated by relatives or trusted colleagues while the real individual is asleep.
Cybersecurity experts suggest that businesses use multiple authentication layers that rapidly escalate in case of suspicious activity. It is especially crucial for financial or password updates.
No Biometric is Foolproof
The 2012 study from the NIST found that iris detection systems used to recognize individuals in a crowd were 1% to 10% unreliable. The missed amounts of actual irises (or false negative mistakes) ranged from 2.5% to 20% or higher.
Recently, in Samsung’s Galaxy S8 Smartphone and supposedly “airtight security,” hackers could circumvent iris-based authentication. Hackers took a digital snapshot of the owner’s face in the night shot mode, printed it out, overlayed a contact lens, and kept the picture in front of the locked phone.
Biometric authentication is not foolproof. It can be accurate, but it is not a perfect system. There need to be several authentication layers, like a mix of passwords, security questions, biometric identity, or biometric identification with government-issued IDs, and the like.
Data Breach
As with anything stored online these days, it seems anything can be breached, no matter how foolproof a system claims to be.
The same is true with biometric authentication. Disclosure of biometric data can put users at permanent risk and create significant legal exposure for the company that loses the data.
In the case of a data breach, any stolen biometric information can no longer be replaced, which is alarming for its real-world implications like identity theft, mistaken identity, and the like.
Companies that use biometric authentication must be accountable for how they secure all the data they collect. Companies must ensure that in every process, including third-party involvement of suppliers and the like, rigidly follow strict protocols for data security.
For instance, payment and financial information must be encrypted directly at the payment terminal. So raw payment card data never touches company servers, reducing data breach and other risks.
If a business should collect biometric authentication security best practices should be applied. Encryption is not a guarantee of security if the applications or users are authorized to access the data being compromised.
What can be leaked from a biometric database, when a database contains almost all kinds of sensitive data available, such as admin access, back end controls and permissions, biometric data, and unencrypted usernames, passwords, and user IDs.
It is difficult to imagine that people yet do not realize how easy it is for hackers to access their accounts. But the more significant threat is what hackers and cybercriminals can do with stolen or leaked biometric data. Once it is stolen, it cannot be undone.
In 2019, there was a huge data breach of over 1 million people in the UK that exposed fingerprints and facial recognition information, unencrypted usernames, and passwords. It is one of the first times a biometric breach of this scale has been reported. This BioStar 2 biometrics data breach exposed 28 million records in total.
BioStar 2 is a web-based encryption platform used worldwide. It has an ability to access central server and endpoint security devices (like facial recognition systems) from any modern internet browser without installing software. It enables easy remote access from mobile devices.
vpnMentor released a report stating that they found 23 gigabytes of data breached in BioStar that included the following:
- users’ pictures attached to their facial recognition data,
- more than 1 million biometric records, username, password, and the like
- client employee records, including personally identifiable information, and records of entry and exit at client facilities.
This breach compromised data from different organizations worldwide, from medical establishments to businesses, companies, and police forces. The vpnMentor researchers stated that BioStar staff were very uncooperative after being notified of the breach, and it took BioStar a week before they took action to secure the database.
This is why robust storage and security systems must be set in place even before a single biometric data is collected. A biometric data breach is not trivial. In the hands of hackers, stolen data can do much damage.
How to Protect Yourself from a Biometric Hack

Biometrics should only serve as a convenience feature for users, or as a second factor of authentication. It is still prone to hacks and data breaches, so here are some ways you can protect yourself from a biometric cyberattack:
1. Use difficult, hard-to-decipher passwords for all your websites, apps, and systems.
You have to presume you are definitely already in the sights of cybercriminals for your facial geometry, fingerprints, and other biometrics. In comparison to a password, the face and fingerprints cannot be reset and cannot be used for a password substitution.
Knowing, however, that the biometric is simply entering the saved password into the login screen of the app, if a cybercriminal wants to hack your online account, they will try to remotely log into the target website with your poor password.
It is why a unique and complicated password must protect all accounts that use biometrics.
2. Use 2FA or Two-Factor Authentication whenever possible.
Besides having strong and unique passwords for every website, you must enable Two-Factor Authentication (2FA).
When protecting your online accounts and personal data, biometrics should only be used as a convenience feature on your smartphone or as a second authentication factor. You need to use biometric authentication sparingly since you can log into many applications with biometrics.
3. Use biometrics in conjunction with a multi-factor authentication (MFA) strategy.
Until sensors and scanners can detect abnormalities, biometrics should always be one component of a multi-factor authentication system.
Multiple measures would complement each other well. Attackers are searching for the easiest ways to enter, so the additional defensive layers can discourage them.
4. Be sure to store all biometric data is secure and encrypted servers and cloud environments.
Small businesses and large enterprises alike are loaded with tons of data. These data play a vital role that is once lost or stolen. It could shut down an entire business. Most businesses rely on cloud-based storage to secure all collected data even after a total system failure.
Ensure you are getting a reliable cloud storage solution with the highest standards of data integrity, protection, and privacy.
Conclusion
Biometric authentication systems are vital to identifying individuals. It has heightened the level of authentication, and it has minimized cases of fraud.
But as with all kinds of technology, biometric authentication has its vulnerabilities. Providers and users need to ensure that data will be collected and managed well, stored securely to minimize and avoid instances of data breach and theft.
Lastly, individuals need to be careful where and when they provide biometric identification. Do not use it as the primary and only measure for identification. Use it with various ID methods to ensure your safety and that which concerns you.
Responsible use of technology, whatever that is, needs to start from us and must begin now.










Leave a Reply