Hackers use vulnerable Jira and Exim servers to infect them in a new Trojan Watchbog Linux version and use the resulting Monero cryptomining botnet.
Wachtbog is a malware strain used to attack Linux servers using vulnerable software like Jenkins, which was discovered by Alibaba Cloud Security researchers, during a May campaign, along with Nexus Repository Manager, 3, ThinkPHP and Supervisord.
Targeted Exim and Jira vulnerabilities
The latest variant found by the Intezer Labs researcher on VirusTotal uses malicious payloads to exploit the CVE-2019-11581 vulnerability of the 12-day-old Jira model injector which leads to Remote Code Execution. The newest version of this variant is found polarly.
It will also abuse the CVE-2019-10149 remote flaw that allows attackers to execute root commands after exploitation–an Exim flaw that is known to have been used in wild at least since 9 June.
According to a current Shodan search, more than 1,610,000 unmatched Exim servers and over 54,000 vulnerable Atlassian JIRA servers could be affected by this attack, as per BinaryEdge.
It is highly dangerous to detect this variant by any VirusTotal scanning engines as the Polarply detected Watchbog sample has an AV detection ratio of 0/55— more information can be found on Intezer Analyze.
#WatchBog botnet (https://t.co/7C6AAtNTXW) spotted exploiting 12-day old #Jira CVE-2019-11581 and #Exim CVE-2019-10149 with Cython-compiled binary.
M5: f839fc8e7f22be30d73286fd665c8c3cPatch Patch Patch!
Added to Intezer Analyze – https://t.co/hWZBCHNjxM pic.twitter.com/6s7bXCfV9d
— polarply (@polarply) July 22, 2019
Infecting Linux servers
The infection process in Watchbog is quite simple because it removes a Monero coinminer from the users efforts to remove it after exploiting the vulnerabilities it targets.
Watchbog downloads and runs malicious pastebin commands after it takes a foothold on vulnerable servers, which will eventually deploy and run the final miner cryptocurrency payload on the compromise Linux box.
The malware will also persist by adding itself to several crontabfiles to ensure you can come back and reinfect system if the user does not get all the crontab that have been changed. Watchbog attack process Watchbog attack (Image: Alibaba Cloud Security).
Watchbog attack (Image: Alibaba Cloud Security)
According to the coin mining setup file, this variant uses the mining pool minexmr.com as well as the previous versions of Watchbog and it collects all the money at the 47k2wdnyBoMT6N9ho5Y7u Qg1J6gPsTboKP6JxfB5msf3jUUvTfEceK5U7KLnWir5VZPKgUVxpkXnJLmijau3VZ8D2zsyL7 address also used during the Jenkins server targeted campaign in May.
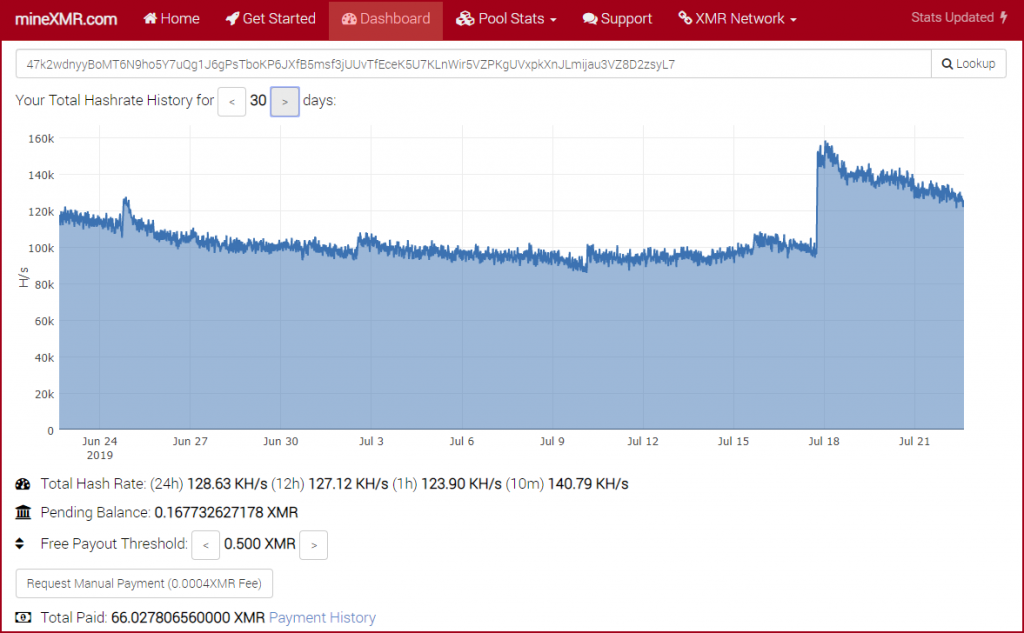
Payment address
Payment address Apart from the no VirusTotal detections and the switching targets to Jira and Exim servers, there is one more thing that makes this specific Watchbog variant special: The malicious scription it uses to drop the coins on compromise Linux servers also includes a contact notation for its victims.
While the attackers would only be able to offer the services in previous versions of the malware to remove an infection promising to send the victims a “cleanup scriept,” “the source of the entry and patch,” this variant notes that “the mission of the attackers is to safeguard the internet.”
The following note is available in the malicious script:
#This is the Old-ReBuild Lady job copy
#
#Goal:
# The goal of this campaign is as follows;
# - To keep the internet safe.
# - To keep them hackers from causing real damage to organisations.
# - We know you feel We are a potential threat, well We ain't.
# - We want to show how tiny vulns could lead to total disaters.
# - We know you feel We are Hypocrite's, because we mine. Well if we don't
how the hell we gonna let you know we are in.
# - Please We plead to evey one out there don't sabotage this campaign
(We want to keep the internet safe).
# - Sometimes you gotta break the rules to make them.
#
#Disclaimer:
#1) We only Wanna Mine.
#2) We don't want your data, or anything or even a ransom.
#3) Please if you find this code, don't post about it.
#4) We make your security better by breaking it.
#
#Contact:
#1) If your server get's infected:
# - We will provide cleanup script.
# - We will share source of entry into your servers and patch (surely).
# - Please if you contacting, please send your affected server's ip and
services your run on the server.
# - lets talk jeff4r-partner[@]tutanota.com or jeff4r-partner[@]protonmail.com
#2) If you want to partner with us ?.
# - Well nothing to say.
#
#Note:
#1) We don't have access to Jeff4r190[@]tutanota.com anymore.










Leave a Reply