This Information Collection Tool was designed to collect e-mails, subdomains, websites, employee names, open ports and banners from various public sources, such as search engines, PGP Key Servers and SHODAN software databases.
This tool is intended to help Penetration Testers to understand the client footprint on the Internet in the early stages of the penetration test. It is also helpful for anyone who wants to understand what an attacker can see in their organisation.
This method was designed to assist penetration testing in an earlier stage and is reliable, simple and easy to use.The sources supported are:
- Google – emails, subdomains
- Google profiles – Employee names
- Bing search – emails, subdomains/hostnames, virtual hosts
- Pgp servers – emails, subdomains/hostnames
- LinkedIn – Employee names
- Exalead – emails, subdomains/hostnames
New features:
- Time delays between requests
- XML results export.
How it functions – System to collect information
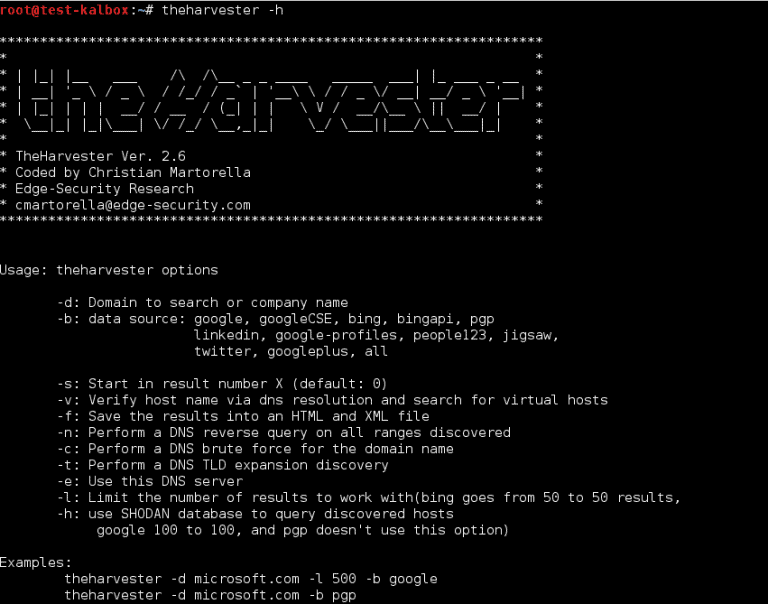
[url] -l 300 -b [search engine name] #theHarvester -d gbhackers.com -l 300 -b google -d [url] will be the remote site from which you wants to fetch the juicy information. -l will limit the search for specified number. -b is used to specify search engine name.
Tool Location:
theHarvester Options:
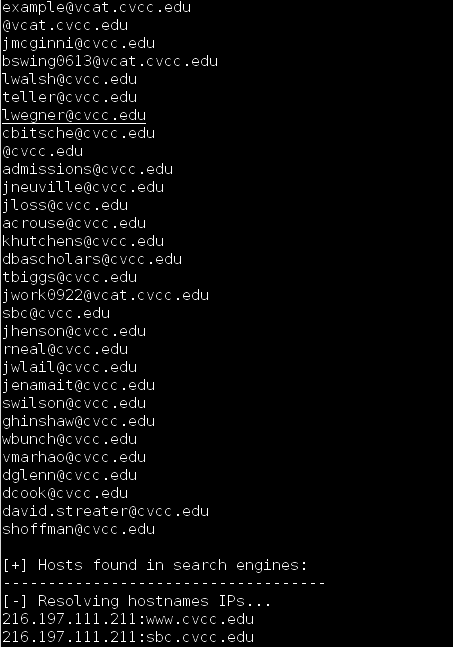
How to Find Email ID’s in Domain:
Example #1:

Example #2:

Download and install the full Harvester kit – GitHub Information Gathering Tool











Leave a Reply