This week Google’s Threat Analysis Group (TAG) shared some data on government-backed hacking and disinformation efforts to targte its clients.
For several years, Google has warned users to State-sponsored hacking attempts and sent thousands of alerts each month.
Shane Huntley, from Google TAG, reported in a blog post published on Tuesday that more than 12,000 warnings triggered by state-sponsored phishing attempts were forwarded to users in 149 countries in the third quarter of 2019. According to the company, the number of warnings is roughly the same as in 2017 and 2018.
In the third quarter of 2019, the United States was the number one goal, followed by Pakistan.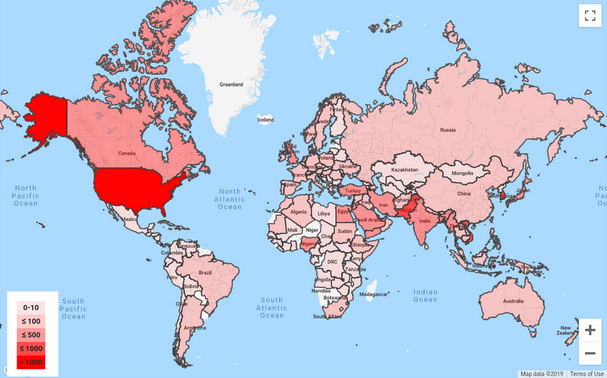
Over 90% of these attacks included attempts to persuade users to transfer their passwords over, including two-factor authentication keys, which would allow the attacker to take over the targeted account.
Google offers an APP service that high-risk users, such as journalists or rights activists, can leverage to better protect their accounts using hardware security keys.
Google’s TAG has monitored activities of more than 270 threat groups that launched targeted attacks or campaigns supported by the government. The activities have been directed at organizations in over 50 countries with the principal objective of gathering intelligence, stealing intellectual property, launching disruptive attacks, monitoring dissidents and activists or spreading false information.
One is Russia’s Sandworm, which in recent years has uploaded several malicious Android apps or tried to upload them to the Google Play Store. In South Korea and Ukraine, some of these applications targeted users.
As regards the disinformation campaigns it recently discussed, Google listed a Russian-based prominent project targeting many African countries and a campaign aimed at the provinces of Indonesia, Papua and West Papua.











Leave a Reply