The rise of technology has brought a new wave of cyber attacks, and one of the most insidious is the DDoS (Distributed Denial of Service) attack. When a DDoS attack hits your website or network, it can be a catastrophic event that leaves you scrambling to get everything back up and running. So how do you counter a DDoS attack? In this blog post, we’ll explore some tried-and-true methods for defending against these destructive attacks so that you can keep your business safe in the digital age.
Defining a DDoS Attack
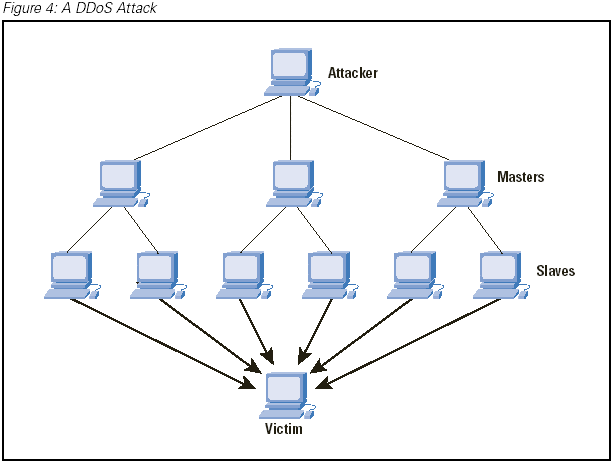
A DDoS attack is an attempt to flood a target device or network with traffic so it can’t handle expected traffic. This can knock websites and other services offline and is often used as a form of cyber warfare. Attackers use many different methods to launch DDoS attacks, but one of the most popular is called an ” SYN Flood .” In this attack, attackers send multiple requests for SYN packets to a target device or network to overload the system and cause it to crash.
DDoS attacks are on the rise.
DDoS attacks are on the rise, and episodes of this nature can be difficult to counter. There is no silver bullet, but you can do a few things to help mitigate the effects of a DDoS attack.
First, make sure your infrastructure is well-protected against these types of attacks. Install antivirus software, firewalls, and other security measures. Make sure your systems are up to date and have backup plans in place in case something goes wrong.
Next, try to identify the source of the attack. Sometimes it is easy to determine who is attacking you – if they are using standard techniques or known malware – but sometimes, it is more complicated. If it is difficult to decide who strikes you, try blocking all traffic from specific IP addresses or Countries.
Finally, remember that sometimes waiting out a DDoS attack will solve the problem. As long as your systems remain operational and you don’t let the attackers cause too much damage, they will eventually run out of steam and stop attacking.
What is a DDoS attack?
A DDoS attack is a cyberattack in which a large number of packets are sent to a target over a short period to overload its servers or disrupt its operations.
There are several ways to counter a DDoS attack. One method is to increase the bandwidth available to your servers, reducing the number of packets sent. Another approach is to use filters and intrusion detection systems to block malicious traffic before it can reach your servers.
Types of DDoS Attacks
There are many DDoS attacks, but they all share the same goal: to cause severe damage to a target by flooding it with traffic.
The most common type of DDoS attack is the SYN flood. This attack works by sending packets with many SYN requests in quick succession. Because routers can only process so many connections simultaneously, these packets can overload the target’s resources and cause it to crash.
Another common type of DDoS attack is the UDP flood. Like the SYN flood, this attack works by sending packets with a high number of UDP requests. However, unlike the SYN flood, UDP packets don’t need to be sent in sequence; they can be shipped anywhere and anytime. This makes UDP floods much more difficult to prevent but also makes them more likely to succeed.
Finally, some attacks use different protocols than TCP or UDP. These attacks, known as custom attacks, are brutal to prevent because they rely on unknown vulnerabilities in the target’s network infrastructure. As a result, custom attacks are usually less successful than other DDoS attacks.
Whatever its type, every DDoS attack relies on one essential tactic: overwhelming the victim’s systems with traffic until they fall over or crash.
How does a DDoS attack work?
When a DDoS attack is launched, the attacker sends overwhelming traffic to a target website or server. This overwhelms the target and causes it to fail, typically by crashing its servers. To counter a DDoS attack, your business must first be aware of the attack and have an initial plan. Once you have identified an invasion underway, you must implement a response plan. Many steps can be taken to mitigate or prevent a DDoS attack from succeeding. Still, the most important thing is to stay informed and update your plan as new information becomes available.
How do you counter a DDoS attack?
First, you need to understand a DDoS attack and the types of attacks that fall under this category. A DDoS attack is a cyberattack that targets a website or server with overwhelming traffic volume. There are three main types of DDoS attacks: SYN floods, UDP floods, and HTTP floods.
To counter a DDoS attack, you first need to identify the type of attack that is happening. It would help if you created a plan to mitigate the damage caused by the attack. The method may include increasing bandwidth capacity, upgrading your firewall, or increasing monitoring and logging capabilities.
What Can You Do to Protect Yourself?
You can do a few things to protect yourself from a Distributed Denial of Service (DDoS) attack:
- Make sure your computer is up-to-date with the latest security patches.
- Be sure to have a robust firewall and antivirus system installed.
- Keep track of which DDoS attacks target websites and avoid visiting those websites altogether.
- Report any suspected DDoS attacks to authorities so that they can take appropriate measures to prevent them from continuing.”
Mitigating Factors for DDoS Attacks
A few things can be done to mitigate a DDoS attack, but understanding the attack and how it works is critical. Always have an appropriate response plan in place and update it as needed. Mitigation strategies include having redundant systems, changing your network settings, and using firewalls.
How to Respond to a DDoS Attack?
There is no one-size-fits-all answer to countering a DDoS attack, as the best response will depend on the specific circumstances of the attack and the resources available to your organization. However, some basic steps that any organization can take to defend against and mitigate a DDoS attack include:
- Establish an incident response plan:Suppose you are aware of or suspect you are experiencing a DDoS attack. In that case, it is essential to create an incident response plan in advance to coordinate the efforts of your team members and ensure that critical systems are protected. A well-planned response will help your organization respond quickly and effectively to an attack, mitigating its impact.
- Diversify your network infrastructure:Your network infrastructure should be diversified to protect yourself from sustained attacks. This means having different networks and servers that can be used as fallback options in case a network is compromised. Additionally, make sure you have up-to-date antivirus software and firewall protections enabled on all devices and servers so that they can detect and block malicious traffic before it impacts your operations.
- Educate employees about cybersecurity threats and how to protect themselves:Please ensure everyone in your organization understands cybersecurity threats, how they work, and how to defend themselves. Teach employees how to report suspicious activity or links online so that they can help protect your organization from potential attacks. Additionally, please provide them with instructions on how to protect themselves from phishing attacks, one of the most common forms of cyberattacks.
- Monitor network traffic and activity:Monitor your network traffic and training to detect any unusual patterns that might indicate that you are experiencing a DDoS attack. If you notice any suspicious activity or links on social media, email, or other online platforms that appear to be associated with the attack, please report it immediately to your security team.
Conclusion
If you are the target of a DDoS attack, there are several ways to counter it. You can raise your security level and add firewall protection to your computer. You can also use antivirus software and keep up-to-date with online safety tips. If you feel multiple computers are attacking you at once, consider using a virtual private network (VPN) to protect yourself from prying eyes. In short, there are many things that you can do to protect yourself from an online attack, but the best way to combat it is always to be aware of what is happening and stay cautious.










FIND US ON SOCIALS