The U.S. Internal Revenue Service (IRS) has not carried out a number of recommended security checks during the years which have made financial reporting and taxpayer data vulnerable to “inappropriate and unrecognized use, modification or disclosure.”
The Government Accountability Office (GAO) finds that 127 recommendations still need to be addressed, most of them from past assessments.
Of these, 107 were taken from previous audits, and 20 were added to the latest assessment. The most important part concerns access controls while others relate to configuration management, task segregation and contingency planning.
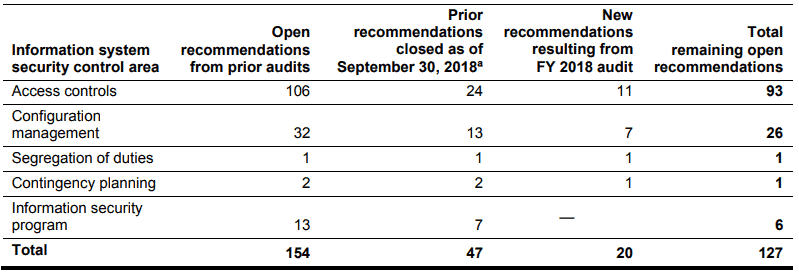
The new recommendations in the GAO report concern 14 new security information system failures in the above areas.
Access controls problems
GAO access control problems found that the IRS still has problems with user identification and authentication, access permission allowances and sensitive information encryption. In these processes, a total of eight shortcomings were discovered.
In particular the IRS has not enforced the use of digitally signed PDF certificates for identification and authentication, including certain tax documents. The Agency also failed to implement its password expiry dates policy and to access certain applications using multifactor authentication.
GAO found on the authorisation side that the app has a function still enabled which is not necessary for business but which allows some user accounts to download the full application’s database or parts.
Another problem is that certain databases that support tax processing systems can be accessed through individual user accounts, though not all of them need this.
Audit by GAO also found that certain servers, email services, and database connections do not have IRS encryption.
Configuration management
IRS also has configuration management problems which, throughout its life cycles, cover security features of all hardware and software components. The issues at hand concern the following:
- Implementation of compulsory access controls for an application;
- update of unsupported data base software and apply vender supplied patches to some applications;
- Constant updating of third-party software on workstations;
- upgrading certain outdated and unsupported software network devices.
Email service managed by one user in admin group
The usual admin group user points to a practice that threatens information security by email services managed in one report of the GAO: auditors found that the IRS had a non-admin account for one of its databases in the admin group.
In addition, only one individual was able to provide an email service to the Agency, which presented clear risks in the event of an unexpected event.
The report concludes that the IRS has overall improved its safety position, but the newly identified inspection defects affect the effectiveness of previously taken steps.
“Until these new and continuing control deficiencies are fully addressed, IRS financial reporting and taxpayer data will remain unnecessarily vulnerable to inappropriate and undetected use, modification, or disclosure” – highlights the U.S. Government Accountability Office











Leave a Reply