Denial-of-service (DoS) attacks are a type of cyber attack that renders computer systems unusable by overwhelming them with traffic or requests. In a distributed denial-of-service (DDoS) attack, multiple computers send this traffic to make it appear that the targeted system has been inundated with requests from many different sources. But is DDoS illegal? And if so, what are some examples of cases where it has led to legal action? In this blog post, we’ll answer these questions and discuss the legal ramifications of carrying out a DDoS attack. Read on to learn more about what you should know about the law surrounding DDoS attacks.
What is DDoS?
DDoS stands for “Distributed Denial of Service” and is a type of cyber attack that attempts to make an online service unavailable by overwhelming traffic from multiple sources. This is done by flooding the target system with requests, making it impossible for legitimate users to access the service.
DDoS attacks often target high-profile websites or services like banks or government agencies. However, they can also be used against smaller targets, such as businesses or individuals. The goal of a DDoS attack is usually to take down the website or service, but in some cases, attackers may also use the attack to steal data or extort money from the victim.
DDoS attacks are illegal in most countries and can result in heavy fines and prison sentences. In some cases, individuals convicted of launching DDoS attacks have also been ordered to pay restitution to their victims.
What is a DDoS attack?
A DDoS attack is a cyberattack in which an attacker seeks to overload a system with requests, rendering it unavailable to legitimate users. This can be done by flooding the target system with requests from multiple computers or using a single computer to send many requests. DDoS attacks often target websites or other online services and cause significant disruption.
DDoS attacks are illegal in many jurisdictions and can result in significant penalties for those convicted of carrying them out. In some cases, DDoS attacks may be considered extortion, as attackers may demand payment to stop the attack.
Why do people commit DDoS attacks?
There are many reasons why people commit DDoS attacks. Sometimes it is to take revenge on someone who has wronged them or to make a political statement. Other times, it is simply because they enjoy the challenge of bringing down a website or causing disruption. Whatever the motivation, DDoS attacks can have serious consequences for the victims.
What are the consequences of DDoS attacks?
There are serious consequences to launching a DDoS attack. First and foremost, it is illegal in most countries. If you’re caught, you could face hefty fines and even jail time. Additionally, DDoS attacks are disruptive and can take a website or online service offline for extended periods. This can result in lost revenue, customers, and opportunities. Some DDoS attacks have also been used as political protest or blackmail.
How to prevent DDoS attacks?
There are several ways to prevent DDoS attacks:
- Use a good firewall and router configuration. This will help to block unwanted traffic and reduce the amount of data that needs to be processed by your server.
- Use rate limiting on your server. This will limit the amount of data processed per second, preventing your server from being overloaded with requests.
- Use denial-of-service protection services. These services can help to identify and block malicious traffic before it reaches your server.
- Keep your software and operating system up to date. This will help to close any security vulnerabilities that attackers could exploit.
Examples of DDoS attacks
There are many different DDoS attacks, and the motivation for launching them can also vary. Some examples of DDoS attacks include:
- SYN Flooding: This type of attack over helical DDoS attack is used to overload a server with SYN requests, essentially tying up all available resources and making the server unavailable to legitimate users.
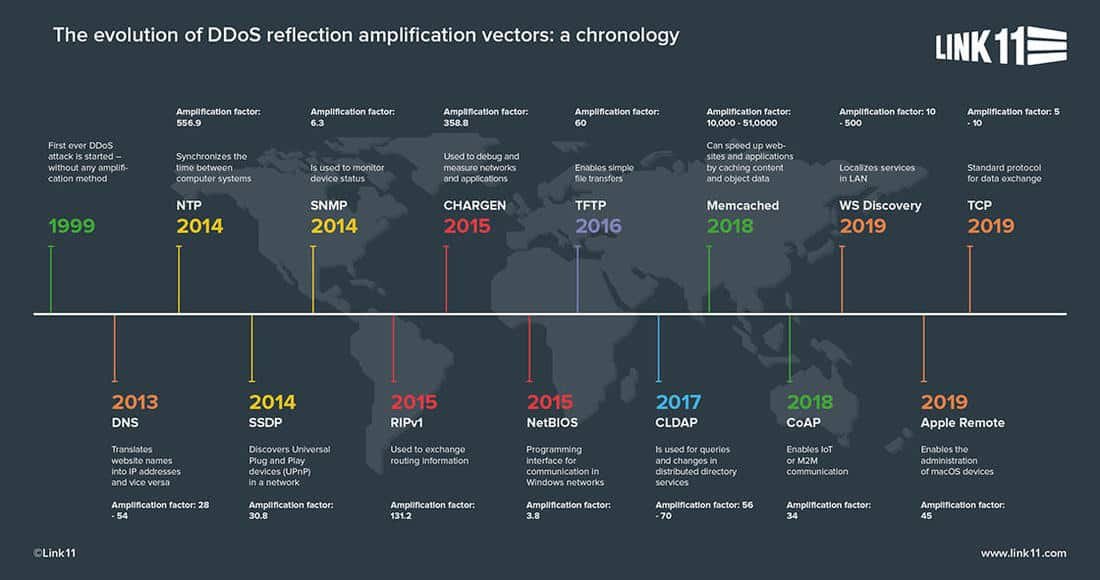
- DNS Amplification: In this attack, attackers send DNS queries with spoofed source addresses to open DNS servers. These servers then respond to the queries with much larger responses sent back to the victim’s IP address, amplifying the traffic and resulting in a denial of service.
- Ping Flooding: As the name suggests, this attack involves flooding a target with ICMP Echo Request (ping) packets. This can quickly consume bandwidth and result in a denial of service for legitimate users.
- Reflection Attacks: Similar to DNS amplification, reflection attacks involve sending spoofed requests to open servers which then respond with large responses that are sent back to the victim’s IP address. However, instead of DNS queries, attackers will use other requests, such as SNMP or SSDP requests.
- Application Layer Attacks: These attacks target specific applications or services on a server, such as a web server or email server. The attacker will send requests that appear to be legitimate but are designed to overload the application or service, resulting in a denial of service.
Is a DDoS attack illegal?
A DDoS attack is a cyber attack in which an attacker seeks to disable a computer or network by overwhelming it with Internet traffic. While there are many legitimate uses for this type of attack, such as testing the resilience of a system, it can also be used for malicious purposes.
So, is a DDoS attack illegal? The answer is not straightforward, as there is no one-size-fits-all answer. In some cases, DDoS attacks may be considered illegal under existing laws, while in others, new legislation may be required to address these types of attacks specifically.
As mentioned above, one of the main purposes of a DDoS attack is to disable a computer or network. This can have serious consequences for businesses and individuals who rely on these systems. For example, if a DDoS attack takes down an eCommerce website, it could lose sales and customers. In addition, DDoS attacks can cause damage to the servers and other equipment used to power the affected system. This damage can be costly to repair and may result in downtime for the business or individual.
Another potential consequence of a DDoS attack is reputational damage. An attacker targeting a high-profile website or company could sully its reputation and cause customers or users to lose their trust. This could have long-lasting effects on their business or brand.
Finally, DDoS attacks can also extort money from the target. A hacker may threaten to launch an attack against a company or individual unless they pay a fee. In this case, the attack itself is not necessarily illegal, but the demand for money would be considered extortion, which is illegal in most countries.
In conclusion, DDoS attacks are not necessarily illegal per se. Still, depending on the context and intent behind them, they may be deemed illegal under existing laws or require new legislation to address them explicitly.
How to protect against DDoS attacks?
There are several ways to protect against DDoS attacks. One is to use a content delivery network (CDN) such as Cloudflare. This will distribute your content across multiple servers, making it more difficult for attackers to take your site down.
Another way to protect against DDoS attacks is to use a web application firewall (WAF). This will filter traffic to your website and block any malicious requests.
Finally, you can host your website on a virtual private server (VPS). This will give you more control over your server environment and make it more difficult for attackers to access your site.
Conclusion
DDoS attacks are illegal and can have serious repercussions if you are found to be responsible for one. All users must understand the potential consequences of cybercrime and take steps to protect themselves from becoming victims or perpetrators. Furthermore, organizations must implement robust security measures to protect their networks from these malicious activities. By educating users on how DDoS works, enacting protective policies and using appropriate tools like firewalls and intrusion detection systems, individuals and organizations can help safeguard against this type of attack.










FIND US ON SOCIALS