A code execution vulnerability has been resolved in the KDE desktop manager by removing the K Config configuration system support for shell commands.
Earlier this week, BleepingComputer in the KDE desktop manager reported on a zero day code execution vulnerability that could allow a remote attackers to execute user commands by tricking them to extract an archive and open their folder. You may use the following free web scanning tool to know the issue directly.
It was caused by.desktop and.directory files supporting shell commands that dynamically assigned a value to different KConfig entries, such as the Icon field. This may enable an attacker to generate malicious.desktop or.. directory files that execute code when a folder is opened by Cybersguards as shown below.
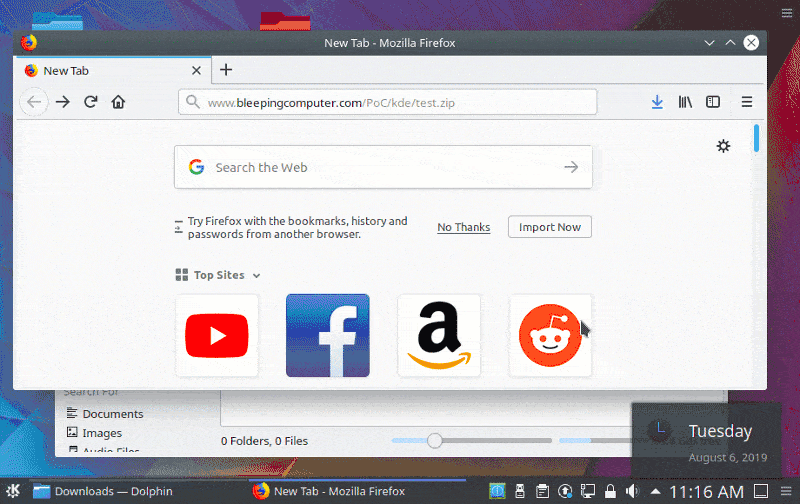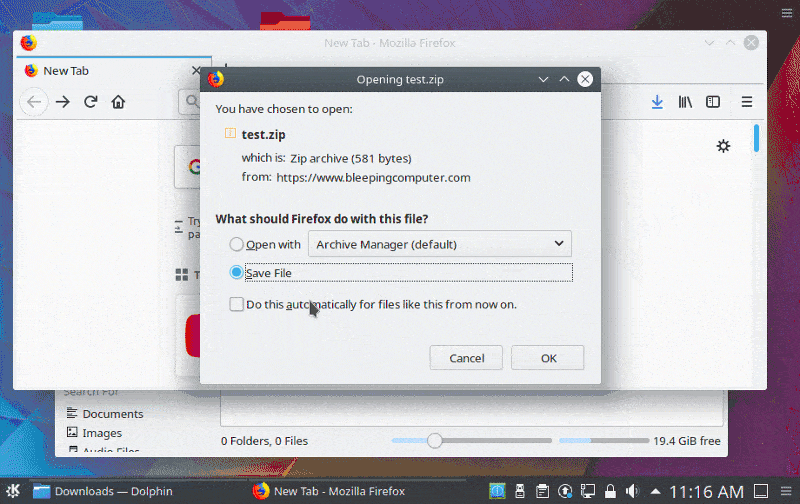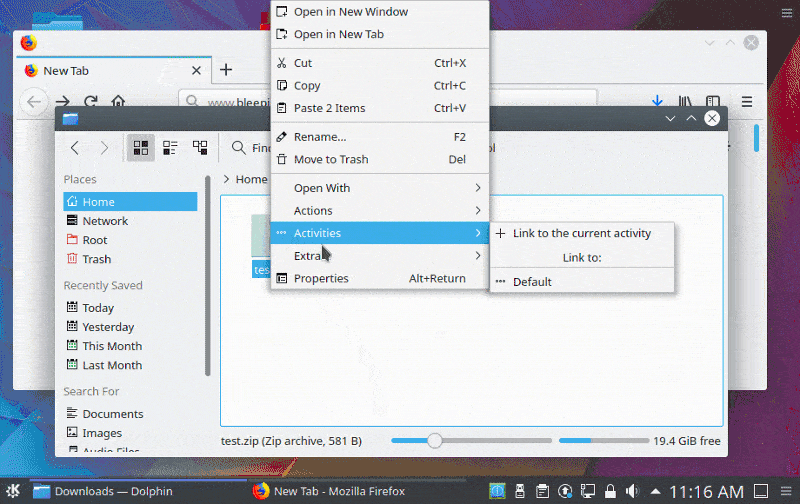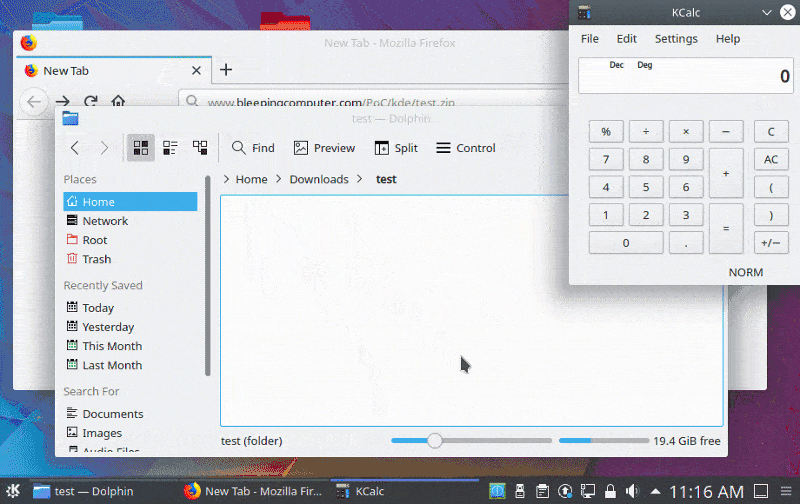
In order to correct this vulnerability, the KDE project has decided to remove support for the shell commands in the KConfig entries.
After careful consideration, the entire feature of supporting shell commands in KConfig entries has been removed, because we couldn’t find an actual use case for it. If you do have an existing use for the feature, please contact us so that we can evaluate whether it would be possible to provide a secure solution.
Note that [$e] remains useful for environment variable expansion.
KDE users can remedy this vulnerability or apply this patch by updating kconfig to version 5.61.0. KDE 4 users should submit this patch. All KDE users are highly recommended to install these updates.











Leave a Reply