Mozilla has patched a vulnerability to the Firefox web browser by launching the 68.0.2 release to enable unlicensed users to copy passwords even if they are password-protected from a built-in Save Logins database of the browser.
According to Mozilla’s Security Advisory, “Saved login passwords can be copied without master entry,” which also rate the safety fault tracked as CVE-2019-11733 as “mild.” Check for mozilla vulnerability scanner here.
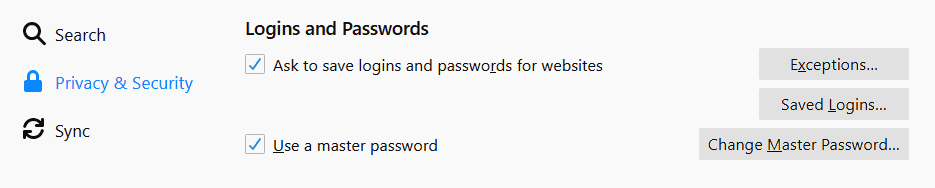
This vulnerability enables anyone with local access to Firefox’s unpatched variant, to access the Save logins dialog in the Firefox Options > Preferences for Privacy & Security menu and to copy the information stored for any of the saved logins using the “Copy Password” option.
Firefox logins and passwords
Exposed unauthorized access to saved logins
“When a master password is set, it is required to be entered before stored passwords can be accessed in the ‘Saved Logins’ dialog,”says Mozilla.
“It was found that locally stored passwords can be copied to the clipboard through the ‘copy password’ context menu item without first entering the master password, allowing for potential theft of stored passwords.”
This happens even though the browser will request the master pass to secure the stored logins from unauthorized access using Firefox.
Firefox 68.0.2 fixes the vulnerability with Mozilla’s security patch, which implies third parties with local access to a Firefox user can no longer steal passwords if a master password is set.

Copying a password
Default turned on without a master password
However, and this is a very significant side note, the password manager of Firefox is activated by default so that customers can save their logins.
While this is a good idea since most people take the most dangerous path to reuse passwords, the downside is that Firefox won’t also ask its customers to set up a password to safeguard their saved records.
It therefore lets people with physical access to their pcs expose their passwords to extremely sensitive data via a browser’s default setup for local attackers.
The excellent news is that the advantages of this strategy are greater than the disadvantage, since the likelihood of someone gaining local computer access is much lower than that of an attacker taking over the accounts of customers, because passwords on other internet platforms have already leaked and re-used.
Another noteworthy thing is that Firefox comes with an automatic update function to ensure that all users automatically patch their browser when Mozilla releases fresh versions that contain safety faults.
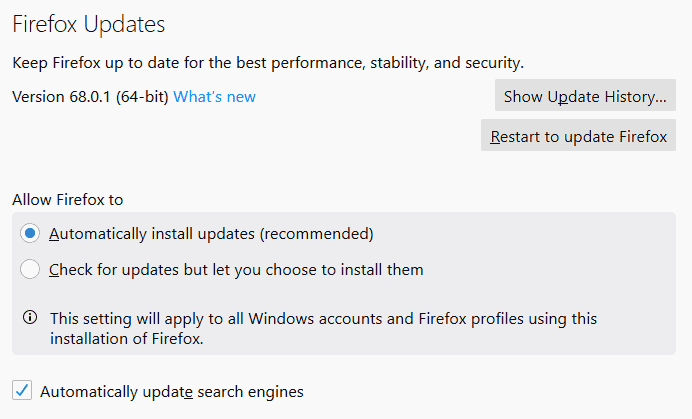
Firefox auto-update
To allow auto-updates, one must go to General preferences and look for Firefox updates where Firefox can install for updates automatically–the suggested option for Mozilla –or check for updates and let users decide to install them.
Although this is the way forward if the recent Firefox safety updates are to be received automatically, the way backfire may also be when one of the upstream applications will also include a bug like the one that disables all addons for users updating 66.0.3 on May 3.
The problem arose from Mozilla, which allows an intermediate certificate to expire in order to sign Firefox addons. Since Firefox needs add-ons to be signed by a valid certificate, all of their add-ons were suddenly deactivated as soon as the certificate had expired.
Mozilla has also remedied a few active zero-day operations in 67.0.3 and 67.0.4 versions, which were later found to be in a chained assault aimed at Coinbase and other cryptocurrency companies, aiming to gain access to their networks.











Leave a Reply