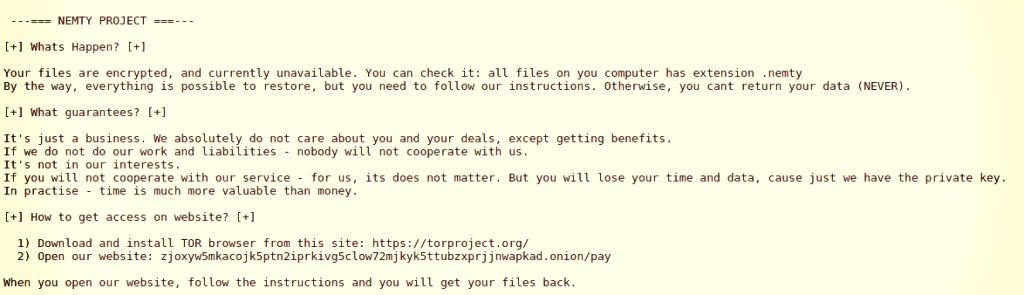
A new ransomware was found during the weekend, containing references to the President of Russia and antivirus software. The scientists call it Nemty.
This is a first version of Nemty ransomware, so it adds files after the encryption phase after the expansion.
The demand for ransom
Like any malware file encryption, Nemty will remove shadow copies for the documents it uses by taking the option of recovering versions of information as produced by the Windows OS.
Victims will see a ransom note that the attackers hold the decryption key and information is retrievable at a cost.
In exams, the demand for ransom was BTC 0.09981, which now converts to around $1,000.
The payment portal is anonymously hosted in the Tor network and customers must upload their configuration file.
Based on this, a link to another website with a chat feature and additional data on the requirements are given.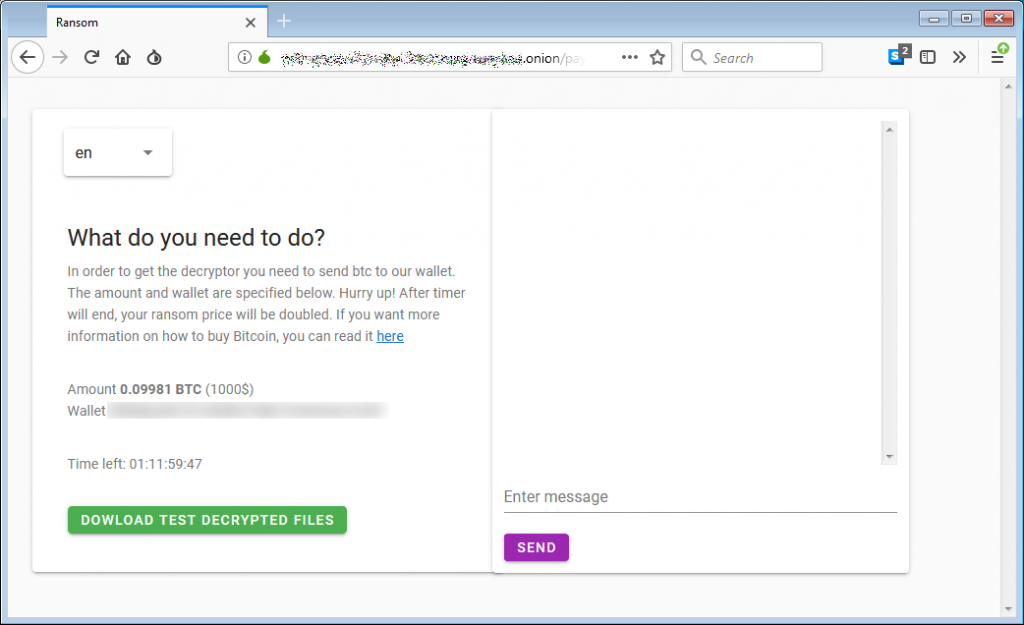
Messages in the code
Vitali Kremez security investigator looked more closely at the malware and noticed the unique name for the mutex item. The author called it “hate,” as can be seen in the following picture.
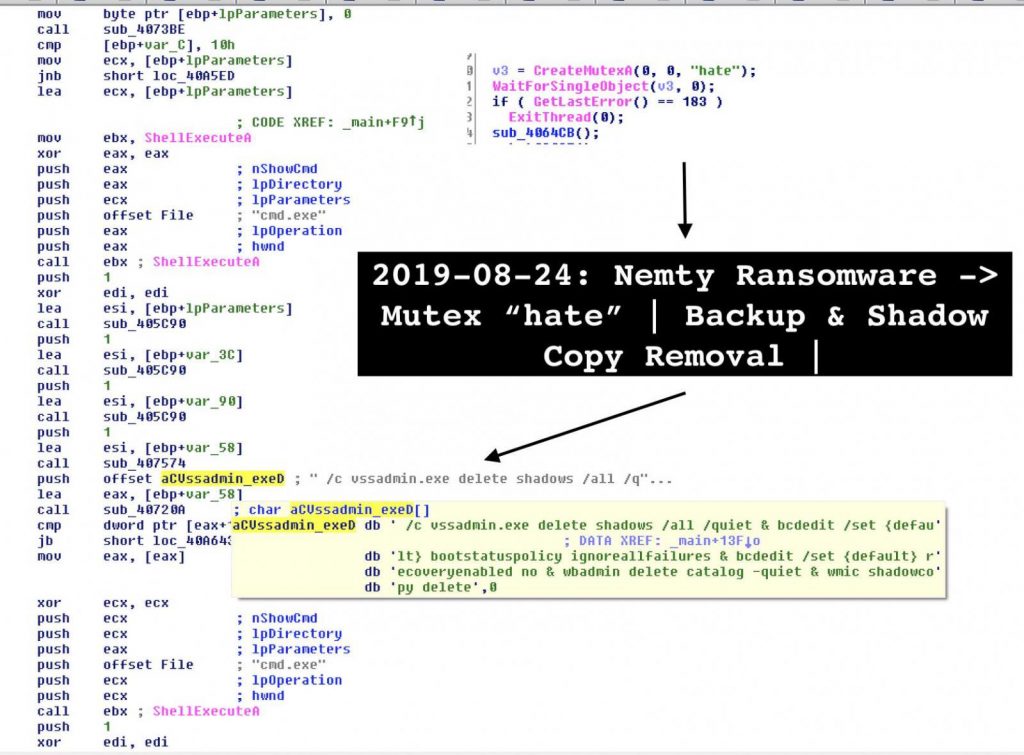
A mutually exclusive object (mutex) is a flag that enables programs to control resources by permitting access to a single execution thread at a moment.
Another strange thing Kremez noted in Nemty’s code is a connection to the image of Vladimir Putin, with a subtitle stating, “I’ve added you to the list of[ insulting], but only now with the pencil.” The investigator discovered a straight message to the antivirus sector.
In the beginning, the reference appeared an odd thing in the code, but in a second look at how Nemty worked, it revealed that it was the key to decoding base64 strings and creating URLs.
How Nemty is distributed is uncertain, but from a credible source Kremez learned that operators use it via compromised remote desktop links.
Unlike the phishing email, which is currently the common distribution method, using an RDP connection controls the assailant, as they no longer have to wait for the victim to take the phishing bait.
Kremez published his Nemty research notes where he listed folders (whatever is needed to boot the OS) and file extensions (binars, shortcuts, and log data) that are not touched by the malware.











Leave a Reply