A fresh malware dropper was noted when computers were infected with a Netwire malicious payload concealed between two benign binders and flying under the radar of most malware alternatives.
“WiryJMPer is a seemingly ordinary dropper with unusual obfuscation. It uses two benign binaries with superfluous jumps and dead branches sandwiched between the binaries to hide its virtual machine, protecting its Netwire payload,” found Avast researchers Adolf Středa and Luigino Camastra.
NetWire (also known as Recam or NetWiredRC) is a Remote Access Trojan (RAT), a Trojan that has been used since 2012 with remote control functionality and a concentrate on keylogging, password robbing, enabling attackers to access and remotely control their pcs.
The uncertain binary
The scientists first realized that the loader was effectively three times the size of the ABBC Coin wallet binary, which it used for the front.
It also came with other warning flags, such as the use of strings from a SoftwareOK built WinBin2Iso 3.16 executable. The fact that WinBin2Iso is a binary image converter and ABBC Coin is a cryptocurrencies based on blocks makes WiryJMPer even more suspicious.
During a closer look using behavioral analysis, Avast scientists found that the uncommon binary was effectively the malware dropper they called WiryJMPer instead of the ABBC Coin wallet.
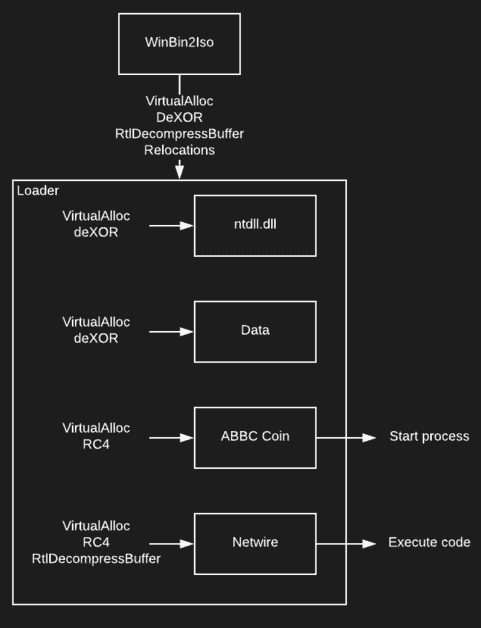
WiryJMPer’s workflow
Virtual stack-based machines
The victim’s machine is infected with a flashy but not unusual way to display program windows in the background to distract the user as Netwire payload drops.
“The first phase of payload appears innocently as a WinBin2Iso binary with a suspiciously big rsrc segment,” the scientists concluded. The JMP instruction, usually included in a loop handling window, goes to a.rsrc section where a roller-coast control flow starts.’
The following step will display a reactive WinBin2Iso window, nearly immediately substituted by a fresh ABBC Coin wallet window, a behavior that scientists have noticed every time the WiryJMPer is introduced at start-up.
“The combination of control flow obfuscation and low level code abstraction made the analysis of the malware’s workflow rather tedious,” Avast’s report also adds.
“Moreover, during the analysis, we found that the obfuscated loader also utilises a (possibly) custom stack-based virtual machine during the RC4 key schedule, which aroused our interest even more.”
The WiryJMPer dropper also attempts to gain persistence on compromised systems by adding a shortcut in the startup folder pointing to its original binary, copied to %APPDATA%\abbcdriver.exe.
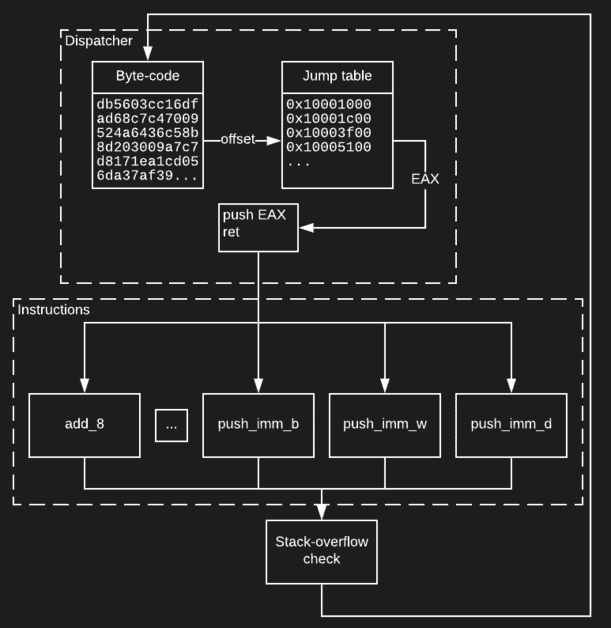
Stack-based virtual machine diagram
The analyzed malware samples always used a “binary WinBin2Iso patched to unpack Netwire and another binary” to lawful cryptocurrency wallets via the payload Decoy.
“While the malware’s functionality isn’t very innovative, it has managed to pass under the radar for some time, probably due to obfuscation and rather low prevalence,” conclude the Avast researchers.
“Rather slow setup of the decoy showing multiple windows with unrelated titles may be suspicious enough for power-users, on the other hand, providing the ‘decoy’ binary might be comforting enough for ordinary users.”
IOCs and past RAT activities
GitHub and at the end of Avast’s WiryJMPer analyzes offer a high level overview of this latest malware loader and a list of compromise indices (IOCs) including malware hashings and Netwire C2 server domains.
Security researchers at the Qihoo 360 Security Center also detected Netwire’s RAT in August when it was distributed through a malscam campaign aimed at several northamerican hotel companies.
In March, scientists of Fireeye found a phishing campaign which provided a payload for Netwire, using the hollow method of evading detection to inject a lawful executable from Microsoft.
In the past, Netwire was used in a campaign targeting payment processors, ATMs and Middle East transaction processing systems via spear-phishing emails[ PDF] as evidence in 2016, as well as collecting payment card information from SecureWorks point-of-sale systems.
Credit:Bleepingcomputer











Leave a Reply