Security providers have released today decrypters for three ransomware infections which allow victims to recover their files free of charge. These decrypters are for Ransomware infections such as WannaCryFake, Yatron and FortuneCrypt.
While none of these ransomware variants saw much wildlife activity, even if one user can get their files free of charge, this is a win.
Emsisoft releases the decryptor WannaCry Fake
Emsisoft published a WannaCry Fake Ransomware decryptor. This ransomware tries to rid on the coattails of the infamous WannaCry infection by adding the extension.want tocry to encrypted files.
“WannaCryFake is a strain of ransomware that uses AES-256 to encrypt a victim’s files. Files that have been encrypted by WannaCryFake are appended with the file extension: “.[][recoverydata54@protonmail.com].WannaCry”.”
Users who are infected will see the following ransom note:

If this ransomware is encrypted, you can download the decrypter to free recovery of your records.
Kaspersky releases Yatron and FortuneCrypt decrypters
Today Kaspersky released Yatron and FortuneCrypt decrypters because of their encryption algorithms weaknesses.
In the past, we discussed Yatron when they began to promote Ransomware as a service. Users who had this ransomware infection would have the. Yatron extension added to their encrypted files.
Since this ransomware is based on HiddenTear, which has known weaknesses in its encryption, Kaspersky says it could generate a decrypter for it. According to Kaspersky, most of the ransomware’s victims are from Germany, China, Russia, India and Myanmar.
“The authors of the ransomware chose the first scenario mentioned above and based their ‘creation’ on the code used in Hidden Tear, a well-known sample of open-source ransomware. According to our statistics, during the last year alone our products have prevented more than 600 infections by various modifications of Trojan-Ransom.MSIL.Tear, with most attacks recorded in Germany, China, the Russian Federation, India and Myanmar.”
Kaspersky also released a decrypter for the FortuneCrypt ransomware mostly targeted Russian Federation, Brazil, Germany, South Korea and Iran.
“During the last year, our products registered more than 6,000 attacks carried out by the numerous variations of the malicious Trojan-Ransom.Win32.Crypren family (FortuneCrypt is part of this family). The top five countries attacked by the malware are: the Russian Federation, Brazil, Germany, South Korea and Iran.”
As this ransomware does not add an extension to the encrypted file names, victims will first be warned when they saw the ransom screen as below.
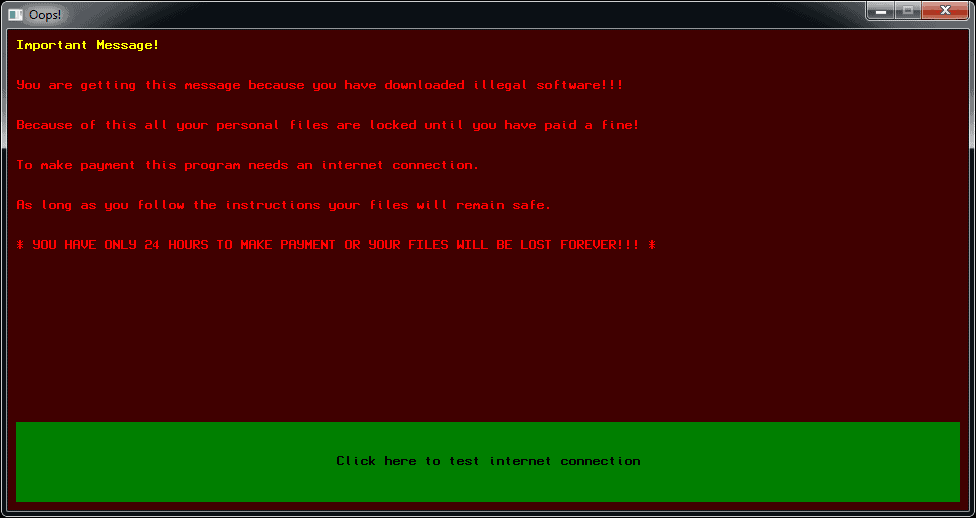
You can download Kaspersky’s decrypters directly from your website or at No More Ransom if you are infected with either the Yatron or FortuneCrypt ransomware infections.











Leave a Reply