A survivor of Muhstik Ransomware hacked back his attackers and released nearly 3,000 decryption keys, together with a free decrypter to get their files back.
An intruder has hacked and encrypted publicly exposed QNAP NAS devices since the end of September. This ransomware was dubbed Muhstik based on the.muhstik file extension.
The intruder would then take 0.09 bitcoins to get his files back, or about $700 USD.
Hacks for Victims home
Upon paying a € 670 rescue, Tobias Frömel, a survivor, said that enough was enough and hacked the attacker’s command and control server back.
Frömel told that the database contained web shells that allowed him to access the PHP script for a new victim to generate passwords. Below you can see the relevant portion of the PHP script from the server which produces and inserts a key into the database.
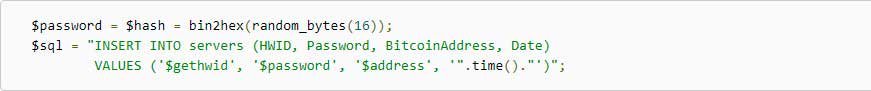 Encryption key generation in ransomware server
Encryption key generation in ransomware server
Frömel told us that he used the same web shell for creating a new PHP file based on the key generator and used it to generate HWIDs special per victim and the 2.858 Muhstik victim decryption keypads stored in the server.
The HWIDs and their corresponding decryption keys were then exchanged with the victims in the Muhstik support and help discussion and the victims in Twitter. This post has a reference to the Pastebin keys and a free Mega decrypter. (Update: See end of article for Emsisoft’s Windows decryptor).
hey guys,
good news for you all, bad news for me cause i paid already... maybe someone
can give me a tip for my hard work ^^
my wallet: 1JrwK1hpNXHVebByLD2te4E2KzxyMnvhb
i hacked back this criminal and get the whole database with keys, here it
is:
https://pastebin.com/N8ahWBni
decryption software:
https://mega.nz/#!O9Jg3QYZ!5Gj8VrBXl4ebp_MaPDPE7JpzqdUaeUa5m9kL5fEmkVs
manual:
upload to nas:
"chmod +x decrypt"
"sudo ./decrypt YOURDECRYPTIONKEY"
and yeah, i know it was not legal from me too but he used already hacked
servers with several webshells on it... and im not the bad guy here :D
but its really sad, i lost 670 € to this criminal :'(
cheers
battleck aka tobias frömelVictims have verified that the decrypter works and they can decrypt their files in our help section.
 Decrypting files
Decrypting files
BleepingComputer also reported that the keys for victims who in the past asked for help can be found on the Frömel database.
This was a good weekend for ransomware survivors, as the HildaCrypt Ransomware keys were also released on Friday.
Update 10/7/19 5:43 PM EST: Emsisoft has released a decrypter running on Windows to decrypt the Muhstik Ransomware encrypted data.
Using the decrypter, you only have to indicate a ransom note on your device and a decryption key will be downloaded automatically from Emsisoft’s servers and attached to the decrypter.











Leave a Reply