CrackQ Password Cracking Manager is a Hashcat interface with a JavaScript and a REST API.
Hashcat is considered the best password cracker in the world. The power of graphical processing units (GPUs) is used to compare imagined plaintext passwords with known high speed password hazards–usually with hundreds of billions of guesses per second–until a match is found. It is an important tool for red teams and pentesters to analyze the strength of the passwords of their customers.
But users will benefit, as all these raw resources, from additional features and better operational management. Cybersecurity and managed security service provider Trustwave has announced the release of CrackQ (alpha version), available from GitHub at Black Hat Europe in London. Developed last year by CrackQ Senior Security Consultant Dan Turner of Trustwave is “an intuitive Hashcat interface with a REST API and a JavaScript web-based application for ease of use.”
Turner was never quite happy with the cracking devices used, and he starts developing his own, just wanting something written in Python so he could add more f Yet CrackQ, a Hashcat password cracking developer, grew into the project. It remains possible to add additional features. Turner has “a multitude of useful features for future releases” and hopes the GitHub community will help in the future.
It does not use shell commands to link to Hashcat, but it uses PyHashcat C bindings directly via libhashcat libraries. This uses SAML2 encryption, which allows MFA to be used, and can also use LDAP. However, while the current version contains features that are not found anywhere else, other systems do not have CrackQ options yet.
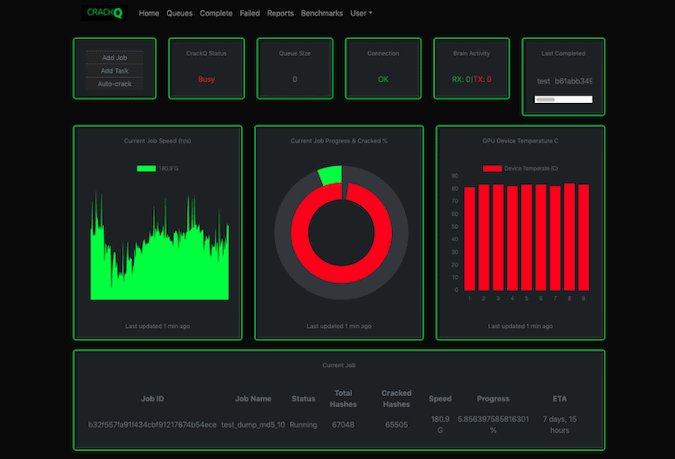
“For example,” says Turner, “it isn’t currently able to work as a distributed system, rather as a client-server set-up. Especially since the distributed crack is not what we required at this point, but it is an API, that could be added easily in the future when I decide to do so.” This gives similar analyzes, but provides visual results and generates a document on demand from the results of a cracking job. The report emphasizes unsafe password choices that allow security teams to remove poor company passwords.
The useful feature is Hashcat Brain integration that is automatically engaged when successful. Brain controls whether a code has already been tested, avoids repeated retries during different cracking processes and improves efficiency for slower algorithms. “However,” Turner said, “the brain is a bottleneck when it cracks at higher speeds. It has a bottleneck of about 500 kH / s, so CrackQ tests the frequency of the selected algorithm and engages the brain when the system is successful.” “A detailed report outlining the weaker areas in a password policy will be included for us,” Turner says. “CrackQ will help us understand it and perhaps help to get the message from bad password choices.”











Leave a Reply