A ransomware attack struck a remote backup of information and encrypted dental practice files in the United States. Hundreds of clients who rely on the backup solution locked their information using Sodinokibi malware encryption.
This occurred on 26 August and affected companies with DDS Safe, a Digital Dental Record (DDS) online backup product that was infected by its cloud management provider, PercSoft.
Progressive data restore
A joint declaration by both firms that manage the medical records reported on Tuesday morning that a decrypter was accessible and that the fix would take between 30 and 4 hours. A subsequent update announced the information restore had begun.
On Wednesday, businesses advised that for some clients, the decrypter was effective and others had to wait for a second version. Some practices were up and running by the afternoon while others were still in the queue.
“Our priority is to get the practice management up and you able to take xrays.” – PercSoft
One might consider that extra secure copies would make retrieval possible as a data backup service.
However, in this case restoration was feasible because the decryption instrument was paid to the carriers of ransomware. Brian Krebs released on his blog a screenshot “subject to a discussion between PerCSoft and the dental office involved,” in which he claimed they paid the ransom.
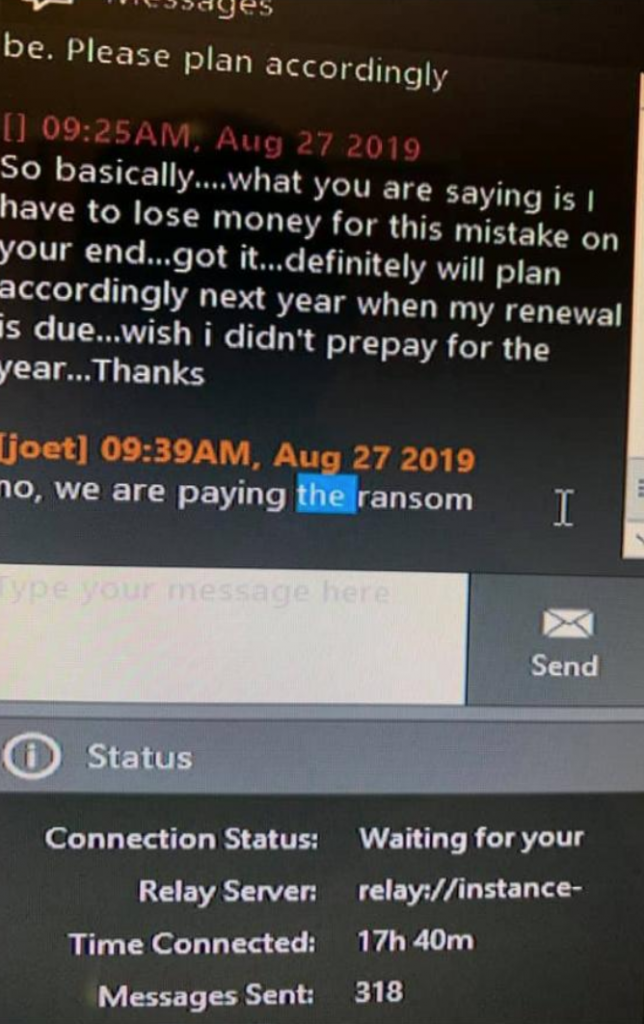
credit: Brian Krebs
The demand for cash has not been made publicly or in private fora, but some customers think PercSoft said it is $5,000 per customer. It is also said that 500 clients were impacted, representing a complete payment of $2.5 million. However, this information may not be entirely accurate.
From Brenna Sadler, communications manager of the Wisconsin Dental Association, Krebs discovered that the ransomware locked information on about 400 dental procedures and that the documents were returned for up to 100.
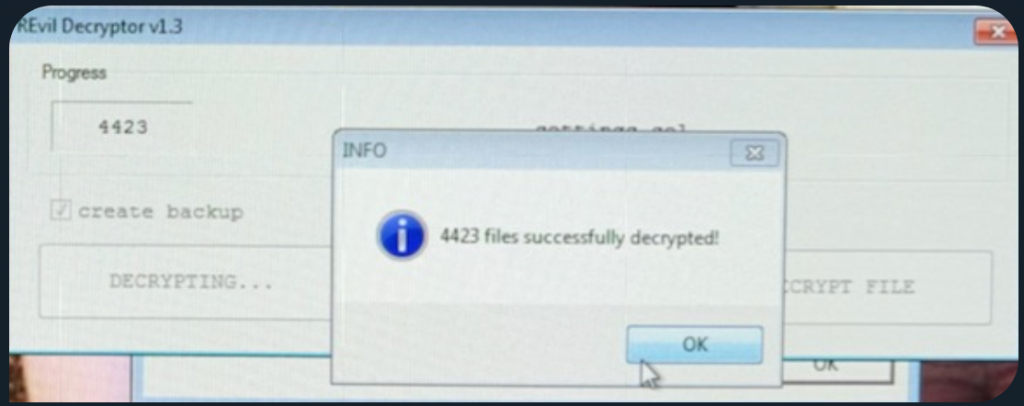
credit: Brian Krebs
The journalist also learnt that Sodinokibi, also called REvil, is the ransomware strain which causes havoc.
Though it was founded in April, Sodinokibi has a reputation and is one of the most active ransomware families today. Unlike many similar malware, Sodinokibi doesn’t depend solely on phishing and also uses vulnerabilities to infect systems.
Credit: Bleeping computers











Leave a Reply