Symantec fixed a local privilege security escalation vulnerability, which pre-14.2 RU2 affected all Symantec Endpoint Protection versions, and allowed attackers to scale down privileges on affected devices and execute SYSTEM privileges for malicious code.
Symantec Endpoint Protection is a series of security solutions for computers and servers, including intrusion prevention, firewall, data loss prevention and malware.
Not the first LPE bug to security vendors
This is not the first local privilege vulnerability escalation problem that SafeBreach Labs Security Researcher Peleg Hadar told a security vendor this year, who also discovered Symantec Endpoint Protection LPE.
Hadar has found similar issues since August, with Trend Micro’s Password Manager, the Endpoint Security Initial Server, the free version of Bitdefender Antivirus and the 2019 Avira Antivirus Software and several McAfee Antivirus solutions.
Both of them may allow hackers to exploit systems that run unpatched versions to drop malicious payloads and to escape detection in the later stages of an attack.
Upon receipt of the study of the researcher, Trend Micro, Check Point Security, Bitdefender, Avast, and McAfee patched security flaws with repair functionality built in within security apps, including CVE-2019-14684, CVE-2019-14684, CVE-2019-8461, CVE-2019-15295, CVE-2019-17449, and CVE-2019-3648.
Failure to escalate permissions set by Symantec
Now monitored as CVE-2019-12758, Symantec Endpoint Protection LPE allows potential attackers to have Admin privileges to effectively exploit this problem in Hadar.
While the risk level for this vulnerability is not immediately evident, these bugs are usually rated as CVSS 3.x base scores of moderate to high severity[1, 2].
Hackers exploit DLL problems for search-order hijacking, such as multi-stage attacks after they penetrate a target computer to boost permissions to further jeopardize the system and to continue.
After successful utilization the system can “bypass the self-defense mechanism of Symantec and reach an escalation in defense avoidance, persistence and privileges, by loading an arbitrary unsigned DLL onto a process signed by Symantec, which runs NT AUTHORITY\SYSTEM,” says Hadar.
Symantec addressed the Symantec Endpoint Protection 14.2 RU2 vulnerability released on 22 October 2019.
Arbitrary unsigned CWD DLL load
Hadar says CVE-2019-12758 comes from the attempt of the security solution to load a DLL from its current working directory (CWD) instead of the current DLL position and from the failure to validate when an electronic certificate is signed for the DLL.
The researcher found that Symantec SepMasterService, running in a signed system, is trying to import DSPARSE.dll from its CWD, the C:\Windows\SysWow64\Wbem directory, in the SysWow64 folder instead of from its actual location.
By using this bug, an arbitrary undeclared DLL could be loaded into the SepMasterService processes if the Administrator’s privileges are already available, thereby bypassing the Symantec Endpoint Protection mechanism.
As the proof-of-concept (Poc) demonstration, Hadar implemented the unsigned 32-bit DLL proxy in a SysWow64\Wbem folder, loaded it and executed it as NT AUTHORITY\SYSTEM processes in a Symantec corporation, bypassing the self-defense mechanism of the Symantec Endpoint Protection as expected.
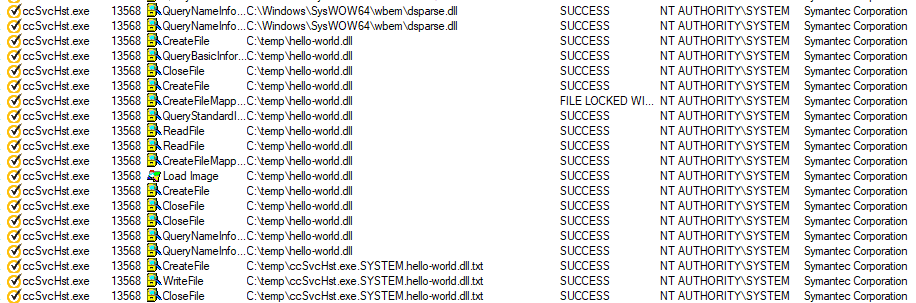
“Attackers are able to load and execute malicious payloads in the context of the signed Symantec process because of the vulnerability,” Hadar says.
“An attacker may misuse this ability for different reasons such as execution or deception such as: Software Whitelisting bypass. Antivirus can not detect the attacker’s binary, because it is attempting to load it without validation.” The CVE-2019-12758 vulnerability on machines running in insecure versions of Symantec Endpoint Protection may also make it possible for the attacker to exploit this ability.
Further data on how the LPE vulnerability was identified, a detailed root cause analysis and a complete time schedule for contact can be found at the end of the Hadar study.
Reference Source:











Leave a Reply