Researchers discovered a Trojan Dropper malicious module hidden inside the Android app, CamScanner, which was downloaded by Google Play Store customers more than 100 million times.
Kaspersky safety scientists Igor Golovin and Anton Kivva discovered the malicious element while looking at the inside of the CamScanner app following a range of adverse reviews published by customers over the recent months.
As a confirmation of sudden rises of adverse scores and user reviews generally point out something that does not precisely work with an app, the scientists discovered “that a development library containing a malicious dropper element was supplemented by the developer.”
Pre-installed similar modules on low-cost systems
This is not the first time that this malicious module type has been discovered on Android smartphones, with pre-installed variants found on over 100 cheap Android devices in 2018 and more than two dozen model phones in 2016.
In both cases, the malicious component was used to advertise infected devices by the threat actors, and unwanted apps behind the users ‘ back were also impaired by Android smartphones and tablets.
CamScanner Play Store entry
In this case, while CamScanner was initially a legitimate Android app using in-app purchases and ad-based monetization, “at some point, that changed, and recent versions of the app shipped with an advertising library containing a malicious module,” says Kaspersky.
The Trojan-Dropper. AndroidOS.Necro.n module is a Trojan Dropper, malware strain used to download and install a Trojan Downloader on Android devices that are already affected, which is able to infect infected smartphones or tablets with any other malware.
When the CamScanner application is introduced on the Android device, the dropper decrypts and executes the malicious code stored on the app’s assets within a mutter.zip file.
“In consequence, module owners can make use of an infected device in any manner they think is appropriate, from displaying the victim intrusive advertising to steal cash from their mobile accounts by billing paid subscriptions,” scientists discovered.
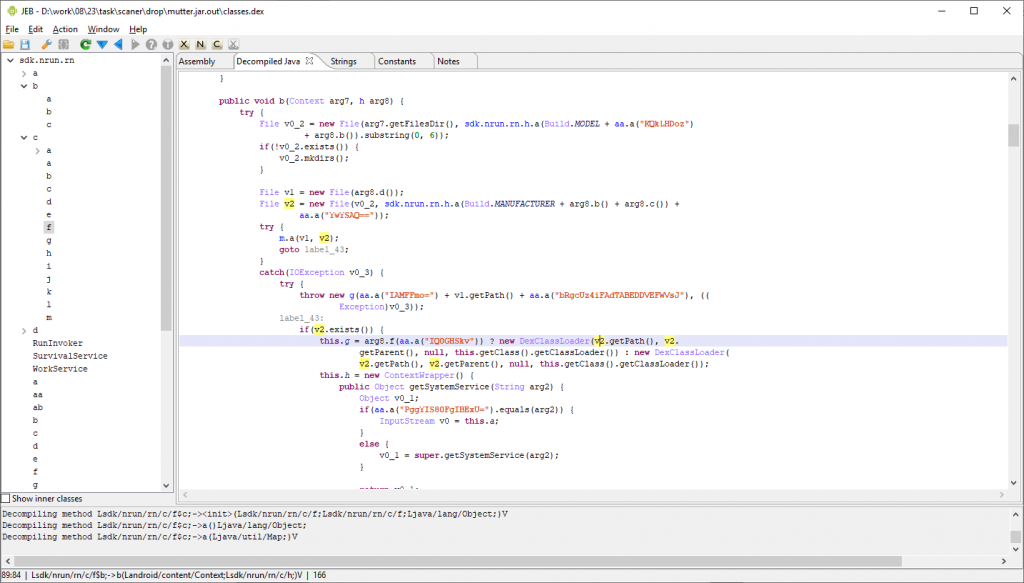 Executing the malicious payload
Executing the malicious payload
Google removed the application from the Play Store after the scientists from Kaspersky had reported their results, but as the scientists also said, “it looks like the malicious code was removed by app designers with CamScanner’s recent update.” “But remember, that app variants differ with distinct systems and some may still have malicious code,” they finish.
At the end of the Kaspersky Report is accessible a complete list of compromise indices (IOCs), including MD5 hashes of malware-distributed specimens and the server domains (C2), used in this campaign.
This is yet another August incident influencing Play Store users: scientists have earlier uncovered a Trojan clicker packed into more than 33 applications in the official Android shop of Google, which have been downloaded more than 100 million times.
Last week, also, an Android app with the AhMyth Android RAT open-source spyware features managed to bypass Google Play Store’s automated malware security twice over a two-week period as identified by ESET scientists.
Credit: Bleeping computers











Leave a Reply