A distributor of malware had planned, before starting Windows, to play a nasty prick by locking the victim’s computers and blame two well known and respected security researchers for infection.
Over the past 24 hours, people unexpectedly realize they are blocked out of their device before Windows begins, after downloading and installing software that appears to be free and break pages.
When locked out, the Computer will show a message claiming that they have been infected with Vitali Kremez and MalwareHunterTeam, both of which are well-known malware and security researchers.
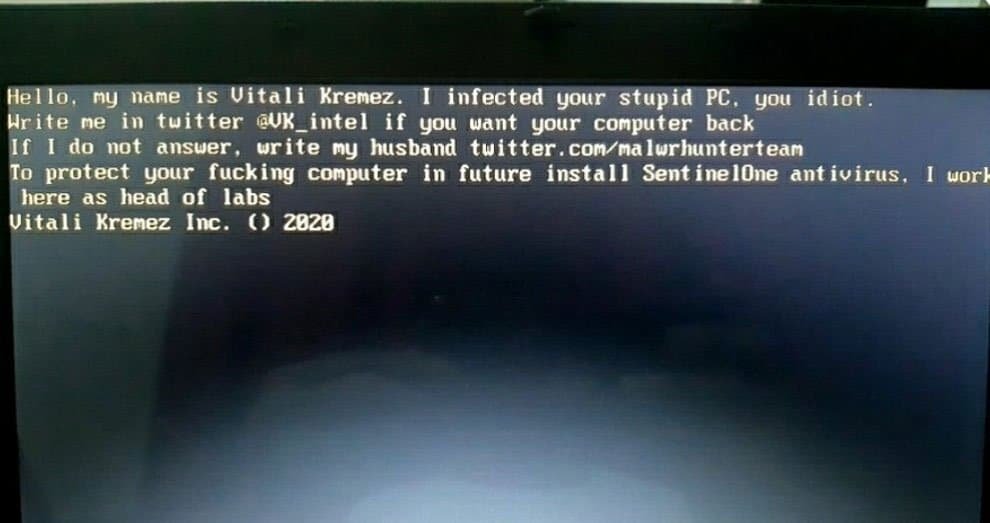
Here is the MBRLocker can be read below:
Hello, my name is Vitali Kremez. I infected your stupid PC. you idiot.
Write me in twitter @VK_intel if you want your computer back
If I do not answer, write my husband twitter.com/malwrhunterteam
To protect your ***ing computer in future install SentinelOne antivirus. I work here as head of labs.
Vitali Kremez Inc. () 2020Another version, which referred to as ‘SentinelOne Labs Ransomware’, is only distributed targeting Vitali Kremez.
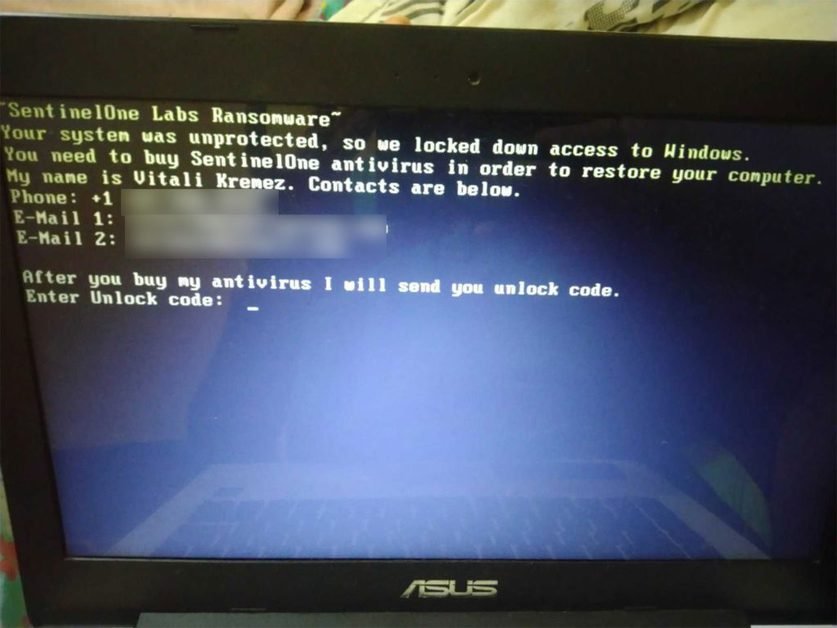
The text of this variant is:
~SentinelOne Labs Ransomware~
Your system was unprotected, so we locked down access to Windows.
You need to buy SentinelOne antivirus in orer to restore your computer.
My name is Vitali Kremez. Contacts are below.
Phone: XXX
E-mail 1: XXX
E-mail 2: xxx
After you buy my antivirus I will send you unlock code.
Enter Unlock code: These infections is called MBRLockers because they overwrite a computer’s master boot log, preventing the operating system from running and showing a ransom note or other message.
This form of infection can be used to keep people from accessing files through ransomware attacks such as Petya or as a destructive wiper.
In this particular case, the name Kremez and MalwareHunterTeam is being tamed by a Malware developer or distributor and published as a harmful prank.
To emphasize, this attack has nothing to do with MalwareHunterTeam and Kremez.
A swarm of MBRLockers was recently produced on YouTube and Discord using a publicly accessible instrument. This method was used for the development of MBRLocker, both to Kremez and MalwareHunterTeam. BleepingComputer claims.
The malware first backups up the original MBR of the device to a safe position until it is replaced while building MTRLockers using this method.
If this wiper uses the same creator, the MBR can be recovered so that people can access the device.
A fail-safe keyboard combination also existed on a sample to ress the CTRL+ALT+ESC keys to restore the MBR and to boot the device at the same time.
We were, sadly, unable to get this malware‘s sample yet to decide whether or not the same builder works.
Please give us a sample, or contact us on Twitter on the website you have downloaded the file if you are infected and know where you downloaded the file.











Leave a Reply