Users can find any material on the worldwide web through the search engines. It helps to easily find information and is a web-based tool for someone to discover or detect information. Here are the best search engines for Hackers.
Different search engines are available online and hackers are used. So here in this article we explain top search engines for hackers.
10 Best Search Engines for Hackers
Shodan
This search engine allows you to explore internet-connected devices, webcams, routers, servers, security, web and much more.
This tool allows you to locate the phones, their locations and their use connected to the internet. In this case, if any client wants to implement market intelligence, shodan can be used.

It is very useful, easy to use and available free of charge. It also promotes virtual footprinting. Shodan also offers a public API to access all shodan information to other devices.
This search engine also tracks the Internet connections.
GreyNoise Visualizer
It is a platform that analyses and assembles information on internet-wide scanners and also allows the focus to be put on targeted scanning and attack traffic.

WiGLE
This search engine is used for the visualization of wireless networks. This merges remote system information to a mid-way server worldwide.
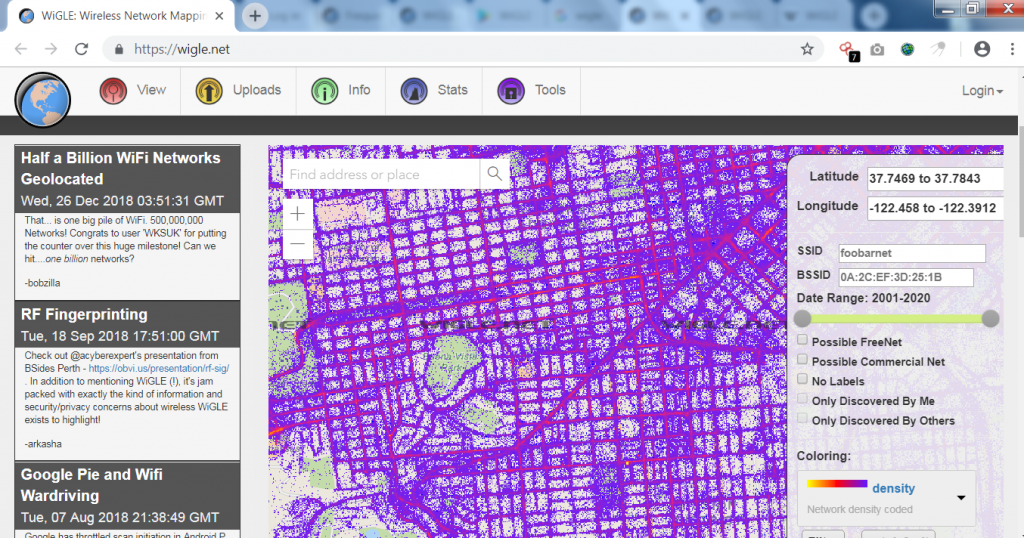
The web applications can update, suspect and map the server via the internet. This device is usually a remote network enforcement stock.
Censys
This search engine allows you to obtain the information you need to monitor the risk and improve safety. It also finds and detects web server versions, database servers, uncatched bugs, routers, versions of OS, insecure services, web application firewalls and more.

This search engine collects information on all web servers to secure each entity on a continuous basis.
Hunter
This search engine helps you find email addresses and connects you to several organizational connections. This is the most flexible and amazing email identification search engine. The primary product is also available with your API.
![]()
This API endpoint helps you to validate the email address delivery.
Pipl
Such search engines recognize the person behind telephone numbers or e-mail addresses. It identifies and finds out all about a person, such as their name, email address, contact information, personal information, professional information and more. This is the largest search engine in the world.
PublicWWW
This search engine is used for source code, as in the HTML, Javascript, and CSS code webpages for verifying or finding signatures, alphanumeric extracts and keywords.
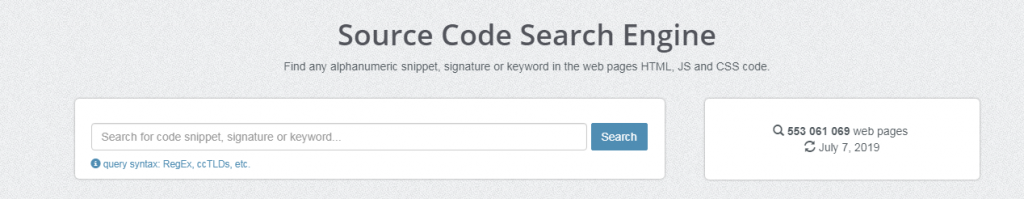
It also has an API for integration developers. It provides millions of search results. If someone wants to find places that use correct images or signs, you can easily find the results from this tool and also download them in CSV format.
If someone uses your composition or not, you can easily recognize and also accept websites that refer to your identity. We can test instances, IP address requests, combine multiple sentences and more.
Zoom Eye
This search engine is used to track site data, administrations, computers, components and more in cyberspace. Used for the identification of systems and their components during the whole day, it is therefore highly useful for investigators to recognise components and dangerous vulnerabilities.

We use only registered information for security research, since this search engine is not designed to target websites and network devices. It is used as a wayfinding (like a navigation chart) in cyberspace.
HIBP
This search engine is called “I’ve been pwned.” Pwn (to be compromised or controlled). This means that the account has been the victim of an infringement of data or is a page that enables Web customers to check whether data breaches have compromised their private information.

This software gathers and analyses numerous dumps and describes the accounts that are reported. This site provides every detail of the data violation and also what kind of information has been involved.
The HBP logo contains the text;–a popular SQL attack sequence. One of the most powerful tools is this search engine.
OSINT Framework
OSINT defined as the “open source intelligence framework,” meaning that it collects information from publicly available sources to be used in the evaluation of intelligence. This search engine is used primarily for national security, business intelligence and law enforcement functions.
This framework includes username, e-mail address, contact details, language transition, government records, name of domain, IP address, malicious file analysis, intelligence of threats and more.
The following are the several submenus from which we can select:
Other subcategories within the section “username” include “username search engines” and “particular sites.” We can further filter down the various services for finding user names by selecting one of these category.
Email Address: We can choose from the subcategories “email search,” “common emails formats,” “email verification,” “vreach data,” “spam reputation lists,” and “mail blacklist” in the section “email address.” We may further filter down the services we have accessible to search for email addresses by selecting one of these category.
“Whois records,” “subdomains,” “Discovery,” “certificate search,” “passiveDNS,” “reputation,” “domain blacklists,” “typosquatting,” “analytics,” “url expanders,” “change detection,” “social anaysis,” “DNSSEC,” “cloud resources,” “vulnerabilities,” and “tools” are all subcategories under “domain name.” Selecting one of these subcategories allows us to limit down the available services and search for domain name information.
IP Address: We can choose from the subcategories “geolocation,” “host / port discovery,” “IPV4”, “IPV6,” “BGP,” “reputation,” “blacklists,” “neighbour domains,” “protect by cloud services,” “wireless network details,” “network analysis tools,” and “IP loggers” in the section “IP address.” By selecting one of these subcategories, we may further filter down the services that are available to us while looking for IP address data.
Images / Videos / Docs: We can choose from the subcategories “images”, “videos”, “webcams”, “documents” and “fonts” within the section “images, videos and docs.” We can further filter down the available services by selecting one of these subcategories. We can then search for any data on the above-mentioned files.
Social Networks: We can choose from the subcategories “Facebook,” “Twitter,” “Reddit,” “LinkedIn,” “other social networks,” “search,” and “social media monitoring wiki” within the section “social networks.” By choosing one of these subcategories, we can filter down the accessible services and search for any data on the social networks we’ve chosen.
Instant Messaging: We can choose from the subcategories “Skype,” “Snapchat,” “KiK,” and “Yikyak” within the section “instant messaging.” We may further filter down the accessible services by selecting one of these subcategories. We next have to look for any data regarding the specified instant messaging networks.
People Search Engines: We can choose between the two subcategories “generic people search” and “registries” within the section “people search engines.” Selecting one of these subcategories allows us to further filter down the accessible services by requiring us to search for any data relevant to the chosen category.
Dating: Within the “dating” section, we can choose from the subcategories “match.com,” “ayi.com,” “plenty of fish.com,” “eharmony,” “farmers only,” “zoosk,” “okcupid,” “tinder,” “wamba.com,” “adultfriendfinder,” “Ashley Madison,” “beautifulpeople.com,” “badoo,” “spark.com,” “meetup,” “black We can delimit or enter the selected website or service by selecting one of these subcategories.
“voicemail,” “international,” “pipl api,” “whocalld,” “411,” “callerid test,” “thatsthem – reverse pone lookup,” “twilio lookup,” “fonde finder,” “true caller,” “reverse genie,” “spydialer,” “pone validator,” “free Carrier lookup,” “mr. number,” “calleridservice.com,” “data24-7,” “hl We may further filter down the available services by selecting one of these category. We can then look for any data about phone numbers.
Public Records: Within the section “public records,” we can choose from the subcategories “property records,” “court / criminal records,” “government records,” and “financial / tax resources.” “birth records,” “death records,” “us country data,” “voter records,” “patent records,” “political records,” “public records,” “enigma,” “the world bank open data catalogue,” and “open.data-portal München.” Selecting one of these subcategories allows us to narrow down the services we have to search for any public data; it is primarily centred on the United States, though there are some possibilities for other countries such as Germany.
Business Records: We can choose from the subcategories “annual reports,” “general info & news,” “company profiles,” “staff profiles & resumes,” and “other resources” inside the section “business records.” We can limit information about and for companies by selecting one of these subcategories.
Transportation: We can choose from the subcategories “car records,” “air traffic records,” “marine records,” “railway records,” “satellite tracking,” and “track-trace” under the heading “transportation.” By choosing one of these subcategories, we can separate information from other categories and modes of transportation.
Geolocation Tools / Maps: Within the section “geolocation tools / maps,” we can select from the following subcategories: “geolocation tools,” “coordinates,” “map reporting tools,” “mobile coverage,” “Google maps,” “Bing maps,” “HERE maps,” “dual maps,” “instant Google Street view,” “wikimapia,” “openstreetmap,” “flash earth,” “historic aerials,” “Google maps update alerts,” “Google earth overlays,” “yand By choosing one of these divisions, we may separate data from several categories and geolocation services.
Search Engines: We can choose from the subcategories “general search,” “meta search,” “code search,” “FTP search,” academic / publication search,” “news search,” “other search,” “search tools,” “search engine guidelines,” and “fact checking” under the heading “search engines.” We can limit down information from several categories and search methods by selecting one of these subcategories.
Forums / Blogs / IRC: We may pick between the subcategories “forum search engines,” “blog search engines,” and “IRC search” under the area “forums / blogs /IRC.” We can delimit and select a service that runs a search on forums, blogs, or IRC by selecting one of these subcategories.
We can choose from the subcategories “web,” “data leaks,” “public datasets,” and “other media” within the “archives” section. We can delimit and select a service that performs a file search by selecting one of these subcategories.
Language Translation: We can choose between the subcategories “text,” “images,” and “analysis” under the section “language translations.” We can delimit and select a translation service by selecting one of these subcategories.
Metadata: We can choose amongst the subcategories “exiftool,” “metagoofil,” “seal,” and “codetwo Outlook export” in the “metadata” section. We can delimit and select a service that does a metadata search by selecting one of these subcategories.
Mobile Emulation: Within the section “mobile emulation,” we can only select the subcategory “Android,” which includes the subcategories “emulation tools” and “apps” within the category “Android.” We can delimit and select an Android emulation service by selecting one of these subcategories.
Terrorism: We may only select the subcategory “Global Terrorism Database” from the area “terrorism.” By selecting this category, we gain access to a terrorism database.
Dark Web: We can choose from the subcategories “general info,” “clients,” “discovery,” “TOR search,” “TOR directories,” “TOR2web,” “web or proxy,” and “IACA dark web investigation support” within the section “dark web.” We can delimit and select a service or information about the dark web by selecting one of these subcategories.
Digital Currency: We can choose from the subcategories “bitcoin,” “Ethereum,” and “monero” under the heading “digital currency.” By choosing one of these subcategories, we can have access to a variety of services and websites that use the digital money we’ve chosen.
Classifieds: Within the “classifieds” area, we can choose from the subcategories “craigslist,” “kijiji,” “quikr,” “ebay,” ” offerup,” “goofbid,” “flippity,” “searchalljunk,” “totalcraigsearch,” “backpage,” “search tempest,” “oodley,” and “claz.org.” We can access different classification services by selecting one of these subcategories.
Encoding / Decoding: The subcategories “base64,” “barcodes / QR,” “javascript,” “PHP,” “XOR,” “cyberchef,” and “functions online” are available under the heading “encoding / decoding.” We can access many services and programming websites by selecting one of these subcategories.
Tools: We can choose from the category “osint automation,” “pentesting recon,” “virtual machines,” “paterva / maltego,” “epic privacy browser,” and “overview” in the section “tools.” We can access different tools by selecting one of these subcategories.
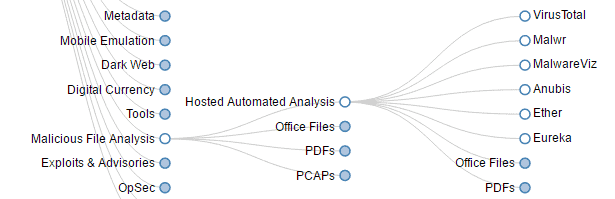
Malicious File Analysis: We can choose from the subcategories “search,” “hosted automated analysis,” “office files,” “PDFs,” “pcaps,” “ghidra,” and “malware analysis tools” in the section “malicious file analysis.” Selecting one of these category gives us access to various malware analysis tools.
“default passwords,” “mitre att&ck,” “exploit DB,” “packet storm,” “securityfocus,” “nvd – nist,” “osvdb,” “cve details,” “cve mitre,” “owasp,” “0day.today,” “secunia,” and “Canadian centre for cyber security” are all subcategories of “exploits & advisories.” Selecting one of these category gives us access to a variety of tools and websites for exploit investigation.
Threat Intelligence: Within the section “threat intelligence,” we can choose from the subcategories “phishing,” “ioc tools,” “ttps,” “ibm x-force exchange,” “malware information sharing platform,” “malware patrol,” “project honey pot,” “cymon open threat intelligence,” “mlsecproject / combine,” “hostintel – keithjones github,” “massive-octo-spice – We can visit many information websites by selecting one of these subcategories.
OpSec: We can pick between the subcategories “persona creation,” “anonymous browsing,” “privacy /clean up,” and “metada /style” under the “opsec” part. We can access various opsec tools and websites by selecting one of these subcategories.
Documentation: We can choose from the subcategories “web surfing,” “screen capture,” “map locations,” and “timeline js3” in the “documentation” area. We can access different documentation by selecting one of these subcategories.
Training: We can choose from the subcategory “games,” “automatingosint.com,” “open source Intelligence techniques,” “plessas,” “sans sec487 osint class,” “netbootcamp,” and “smart questions” under the heading “training.” We can access different training sites on the given topic by selecting one of these subcategories.
OSINT Framework, as you can see, is more Wikipedia-style in terms of the number of menus and categories it provides, allowing us to locate practically any category of what we’re looking for. We strongly advise you to give it a shot.
Types of Hackers
There are four main types of hackers: white hat hackers, black hat hackers, ethical hackers, and script kiddies. White hat hackers are responsible for finding and resolving security flaws before they can be exploited by malicious users. Black hat hackers seek to exploit vulnerabilities for personal gain or to cause damage to systems. Ethical hackers try to adhere to the principles of ethical hacking while still achieving their objectives. Script kiddies are not considered hackers in the traditional sense but rather computer experts who use scripting languages such as PHP or Perl to automate repetitive tasks on the web.
Methods Used by Hackers
Methods Used by Hackers to Find Information Online
There are many different methods hackers use to find information online. Some of these methods include:
- Searching the web for keywords related to their target.
- Conducting searches on specific websites with the intention of finding vulnerable software or information.
- Finding security vulnerabilities in websites or software and exploiting them.
- Looking for private information, such as login credentials, on popular websites.
- Exploiting known vulnerabilities in computer systems to gain access to confidential data or networks.
The Costs of Cybercrime
Cybercrime is a growing problem and search engines are an important tool for law enforcement and cyber security professionals. In this blog post, we discuss the costs of cybercrime and how search engines can help to identify offenders.
Cybercrime costs businesses and governments billions of dollars each year. The FBI states that cybercrime cost U.S. businesses $55 billion in 2016.[1] Worldwide, the total cost of cybercrime is estimated at $450 billion annually.
One reason cybercrime costs so much is that it often targets businesses and governments with sophisticated attacks that can cause significant damage. For example, in December 2016, hackers stole data from over 100 million customers of credit-reporting agency Equifax.[3] The attack was especially costly because it exposed personal information such as Social Security numbers and birthdates, which could be used to commit fraud or other crimes.
Search Engines for Hackers
As the cost of cybercrime increases, so does the need for search engines to help investigators track down offenders. One way search engines can assist in this effort is by helping to identify online activity associated with specific crimes.
Conclusion
As the world becomes more digitalized, it becomes increasingly important for businesses and individuals to take measures to protect themselves from cybercrime. Search engines are a critical part of this process because they provide access to a wide range of information that can be used for nefarious purposes. By understanding how search engines work and how hackers use them, you can better protect yourself as well as your business.











Leave a Reply