Attackers target companies from the utility sector using the malware Adwind Remote Access Trojan (RAT) using a malicious URL redirection campaign.
Adwind (also known as jRAT, AlienSpy, JSocket and Sockrat) has been distributed to threaten players under the malware as a service model (MaaaS) by its designers, and is able to prevent detection by most important anti-malware methods.
While the Adwind Trojan does not detect malware-related alternatives, antivirus software based on sandbox and behavior should be able to detect and block it effectively.
Targets home and company users
This enables operators to compromise their targeting pcs effectively without suspicion and carry out a variety of malicious duties, from stealing sensitive information such as Chrome, IE and Edge VPN certificates and credentials to capture and exfiltrate the keystrokes of victims.
The Adwind RAT can also record video and sound as well as snap photos with the webcam of the infected machine, and cryptocurrency cryptocurrency information mine.
Since 2013 Adwind has been conducting rounds of assaults targeting hundreds of thousands of people and organizations in a wide range of sectors including finance, telecommunications, software, energy, and government.
From previously detected malicious campaigns, spam emails containing infected attachments or links redirecting the targets to the primary payload are the initial vector used mostly by the attackers who drop Adwind on their target systems.
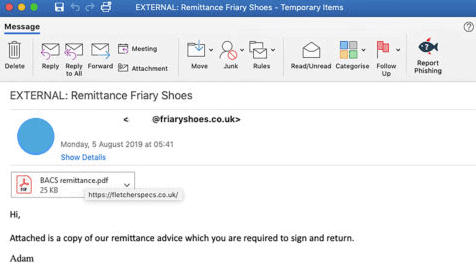
Sample malspam email
Malicious URLs camouflaged as PDF attachments
E-mail messages were discovered in the personnel boxes of businesses from the utilities industry that are used to infect the victims of this particular campaign and land there after effectively bypassing e-mail gates of the businesses.
They are sent via a compromised e-mail account at Friary Shoes. The servers of the company are also used to store and send malware to the victims ‘ pcs via Adwind.
“The top of the email is an integrated picture, which looks like a PDF file attachment, but actually is an jpg file with a built-in hyperlink,” Cofense scientists discovered.
“When victims click an attachment they are transferred to the infection URL hxxps:/fletcherspecs[.]co.[.]uk / in which the original payload is downloaded.” The attackers use the email box to trump the objectives by pressing the malicious connection disguised as a PDF attachment:
![]()
C2 beacon traffic
After pressing the download connection in the malspam email, the first payload will be dropped on the target device in the form of Scan050819.pdf obf.jar JAR.
The malware will instantly contact their C2 server and add all the information collected in the folder C:\Users\Byte\AppData\Local\Temp\ along with its dependencies.
The next step in the infection chain is to identify and destroy any well-known analytics and anti-virus software using the lawful Microsoft taskforce to end one or more procedures.
The end of the Cofense document includes compromise indicators, including malware samples, malicious URLs used for phishing attacks and related data.
Switching methods and baits
Cofense scientists have also noted several other coordinated assaults using a wide range of methods and appetites for phishing different target kinds.
Just last week, they found a spear phishing campaign around a Microsoft e-mail gateway using files that were shared through the Google Drive service and aimed for employees of an energy industry business.
In July, when the malicious URLs were switched, they generally used WeTransfer notifications to bypass the Microsoft, Symantec and Proofpoint established e-mail gates.
A basic HTML element has also been used to hide phishing page connections from antispam alternatives, which enabled the safety checks for Office 365 Advanced Threat Protection to be avoided and phishing mails to be sent to customers ‘ inboxes.
Another campaign using fake eFax emails was identified in early July during a banking Trojan and RAT cocktail infection with malicious Microsoft Word document attachments.
Cofense also discovered a phishing campaign which used QR codes a month previously, whereby its operators redirected prospective objectives to landing pages and avoided safety alternatives and controls aimed at stopping assaults.











Leave a Reply