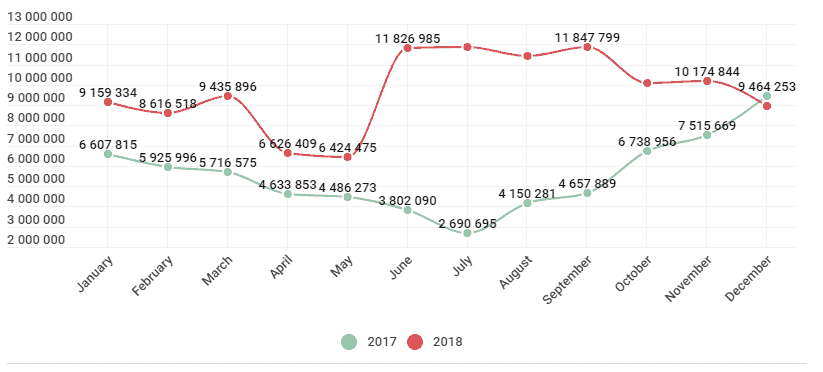
Mobile users were targeted by nearly twice as many attacks using malicious software in 2018, rising from 66.4 million in 2017 detected events in 2017 to 116.5 million by the end of last year, according to a Kaspersky Lab report.
Although the number of malicious mobile software attacks is increasing considerably, only 5,321.142 Malware-sample installation packages were found all year long, down 409,774 compared with statistics for 2017.
Threat actors who have decided not only to target mobile users but also to use highly tested methods such as SMS spam, were also ready to experiment with techniques such as DNS hijacking, previously reserved for the attack of desktop platforms.
The most popular tools and techniques for attacks in the arsenal of mobile errors were, as detailed in Kaspersky’s report: as a side note, the security company also was able to detect three malicious campaigns run by advanced persisting threat groups, who sniffed messages on their victims ‘ mobile devices on various social networks.
Kaspersky is not the only safety company that has uncovered this type of APT activity, but the research team at CheckPoint is also developing a wide-ranging surveillance operation spanning two years targeting different groups of people using malicious mobile apps to exchange sensitive information from the device and voices from their surroundings.
“Droppers (Trojan-Dropper), designed to bypass detection
Attacks on bank accounts via mobile devices
Apps that can be used by cybercriminals to cause damage (RiskTool)
Adware apps”
Throughout 2018, bankers and droppers both saw a steady increase in the number of single samples detected and in the number of users attacked with their help. Although Trojan-Dropper. AndroidOS.Piom was the most “popular” dropper family among threat actors, the Asacub and Hqwar banking trojans were the most prevalent.
Although mobile banking Trojans also abused Accessibility Services in advance, 2018 saw a drastic upswing in this malicious technique enabling malware creators to “hijack a perfectly legitimate application and force it, say, to launch a banking app to transfer money right there on the victim’s To be more precise when it comes to actual numbers, Kaspersky reports that all, In particular, they place their components in the system area of the device, to which the user has only read access, and therefore they cannot be removed using regular system tools.
“5,321,142 malicious installation packages
151,359 new mobile banking Trojans
60,176 new mobile ransomware Trojans “

“Finally, Kaspersky Lab detected the technologies and products used in 2018 to fend off mobile malware: the statistical data behind the 2018 Mobile Malware Evolution Report of Kaspersky Lab was collected using Kaspersky mobile security solutions.










Leave a Reply