The Cyber Awareness Challenge, which is also known as the Army Cyber Awareness Course, the cyber awareness challenge or the DOD cyber challenge, is an annual information security training that was developed to raise cyber awareness among Department of Defense (DoD) employees.
It’s available online, it’s free of cost for everyone, and it’s also accessible from any part of the world so long as you have a reliable internet connection!
Everyone with a computer or who manages some kind of confidential information will benefit from it. In this guide, we’ll explore the key lessons of the DoD cyber challenge and the summary of the entire training materials.
DoD Cyber Awareness Challenge: Who Can Take It?
- Army, other armed force branches, government employees.
- Companies and companies should view this cyber literacy challenge as an outstanding opportunity to deliver cybersecurity instruction to their workers.
- All individuals — especially those who value privacy and security, who work with sensitive information, or those who work in the IT field — should take this training to protect themselves and their clients from potential cyber-attacks.
The Format and Main Content of the DoD Cyber Awareness Challenge
There are three main sections and their subsections in the DoD Cyber Awareness Challenge tutorials:
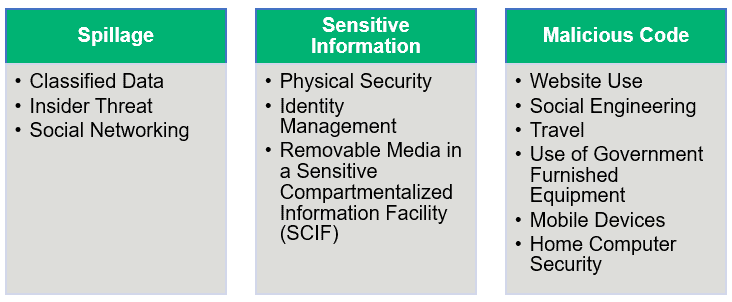
In order to deter a cyber threat, each section has concepts, vulnerabilities, real-life situations, and talks about the kinds of choices you can make or stop.
Data Spillage
Spillage” in the government is a term that refers to information leaked from a higher classification or level of protection to a lower one.” A spillage places national security at significant risk. Spillage happens when someone inadvertently or purposely makes an unwanted leak of information, alteration of records, or engages in surveillance, resulting in the failure or depletion of resources or capabilities.
Sensitive Information
It is important that you do whatever you can to secure this information with any kind of company or entity that treats confidential information, both for the sake of your clients and to stay consistent with laws and regulatory data security standards. Several of these statutes include:
- The Health Insurance Portability and Accountability Act (HIPAA),
- The European Union’s General Data Protection Regulation (GDPR),
- The California Consumer Privacy Act (CCPA), and
- The Payment Card Industry Data Security Standards (PCI DSS), etc.
But what is “sensitive information” considered? “Sensitive data includes:
- Controlled technical information (CTI),
- Personally identifiable information (PII),
- Protected health information (PHI),
- Financial information,
- Personal or payroll information,
- For official use only (FOUO),
- Controlled unclassified information (CUI), and
- Proprietary data.
It is important to secure these forms of classified information because their disclosure will damage government missions or interests. Such sensitive material, for example, contains details or information supplied by a confidential source (person, company, or foreign government) on condition that it is not published.
Examples of these categories of knowledge for corporations and healthcare organizations include:
- Names, emails, phone numbers, etc. of staff or clients,
- Financial statements and details about the account,
- Credentials and passwords for users,
- Hospital history for patients and health-related information, and
- Data from Medicare or insurers.
Malicious Code
By uploading compromised email attachments and directories, or accessing infected websites, malicious code may be distributed. Viruses, Trojan horses, viruses, macros, and scripts contain malicious code. They can harm or delete digital files, erase your hard drive, and/or allow hackers from a remote location to access your Laptop or smartphone.
Key Lessons for Corporations and Individuals from the DoD Cyber Awareness Challenge
Here, we have written a summary of training for cyber awareness challenges, covering the key takeaway lessons.
Please note that we have included only handpicked lessons for a general audience that we consider beneficial. It doesn’t have all of the course’s teachings, though. You must complete the DoD Cyber Awareness Challenge yourself to get access to all that!
Protection Against Malicious Code
Malicious code is a term describing the code used in online forms, scripts, and software that in some way aims to cause harm. Here are some helpful tips to help your staff avoid the risks associated with the download and installation of malicious code:
- Before uploading them to your computer, scan all the external files.
- In a suspicious email or pop-up generated by an email message, do not access website links, buttons, and/or graphics.
- Contact your security point of contact (POC) or help desk for assistance if you suspect an email is malicious or if any unknown/unauthorized sender requests some personal/sensitive information.
- Research any application and its vulnerabilities before downloading it for your personal and office equipment (laptop, PC, mobile, etc.).
- View a plain text email and do not display an email in the preview pane.
- If your organization uses an email signing certificate, look for digital signatures (highly recommended). Emails that are digitally signed are considered more secure.
Best Practices for Protecting Sensitive Information
When you trust your staff to handle the confidential information of customers, they must be conscious of the data’s sensitivity and how to protect them. A single negligence act can be disastrous. Here are several big takeaways from the challenge of cyber literacy that you can use to educate workers.
- Ensure the recipient is at the receiving end while faxing sensitive data. To confirm the receipt, contact the recipient.
- A failure to encrypt PII-containing email messages is the most widely recorded cause of PII breaches. So, when sending PII, PHI, or some other personal information, use encryption at all times. In addition, digitally signed emails provide authentication whenever possible and ensure the integrity of information.
- Prevent confidential information from being saved in private files or shared programs (e.g., SharePoint, Google Docs, etc.).
- For transmitting PII and PHI, never use personal email accounts.
Only approved information systems store confidential data. Do not, on non-authorized systems, transmit, store or process confidential information.
Follow the policy of your organization concerning the retention or disposal of sensitive data. - It is likely that mobile devices could be compromised or malware corrupted. So, please use your organization-approved mobile devices and follow the rules of your organization on the use of mobile operating devices and security when working with PII or PHI.
Prevention Against Insider Threats
According to data from the Ponemon Institute and ObserveIT, events relating to insider attacks are up 47 percent since 2018.
The word insider danger applies to a scenario under which the workers themselves leak the data (intentionally or unintentionally) or commit cybercrime against the company. You should not rule out the risk of internal attacks because the staff has on their hand’s lots of information freely accessible to them. So, as an employer, you must keep an eye on the actions of your workers and also prepare the employees to understand the possible danger that might arise between them. We’re not saying that the workers are all insider threats. However, their mental distress may make them a possible choice to become one while someone is going through tough life conditions or having recurrent interpersonal problems. Observe them and determine if they exhibit any unusual or linked habits, such as:
- Showing conduct that is offensive, vindictive or illegal, or
- Having an undue or uncommon interest insensitive or sensitive details
- Showing mysterious or unexpected riches by sales of high-value products/living above one’s means or assets
- Trying, without the need to know, to view and/or delete confidential information
Report any unusual activities or actions in compliance with the insider danger protocol of the department, instead of having the benefit of the doubt.
There are, of course, additional precautions you may take to stop or limit the influence of insider threats:
- Perform risk analysis across the enterprise.
- Establish a data usage policy and implement it.
- Implement the concept of least privilege in order to restrict employee access to only the programs available.
- Check access lists regularly and withdraw access automatically for staff who leave or are fired.
- Using a Security Information and Event System (SIEM) to monitor the activities of workers and the details they enter.
Best Practices for Physical Security in the Workplace
For organizations, there are several reasons why physical protection is so critical. Your colleague may be an internal threat, or other walk-ins or guests maybe hacking, eavesdropping, or searching for an excuse to intercept important data from files or devices. Such accidents occur not only in military buildings but also within organizations. So, you must be careful with your wellbeing in the office, too. It implies:
- Don’t chat outside the office about work/customers/company practices about ads, infrastructure, etc. Any classified information that must not go out maybe accidentally exposed by you. Be vigilant when sharing classified material, such as PII or PHI, even inside a closed work environment, as persons without a desire to know may be present around you.
- When downloading texts from smartphones or other media, be mindful of people eavesdropping.
- Know and observe the rules of the organization to gain access into the facility, protect the work environment, and respond to emergencies.
- Often lock the cabinets and drawers of the office if they have any files/papers containing classified material.
Best Practices for Portable Devices and Removable Media
Portable computers and removable media pose a serious security danger to corporations as well as government agencies. They’re comfortable and easy to use. However, without the consumer understanding it, portable devices can even bring malware from one computer to another. So, if you insert an infected computer into a new system, the malware could be mounted on the new device.
Flash media, such as thumb drives, memory cards, and flash drives, portable hard drives, compact disks, and external audio players such as iPods, contain all kinds of media.
So, what should you do for your organization’s protection?
- Only use disposable media to contain, as operationally necessary, work-related data owned by the company and authorized in compliance with policy by the relevant authority.
- Encrypt data correctly while it is stored on a portable media unit.
Do not use any disposable privately owned/non-organizational media to store the data of the organization. - Mark all removable media as best practice, especially if they contain PII, or PHI, or any sensitive data.
- Avoid loading removable media into your device with unknown content.
- Respect the strategy of the company to sanitize, purge, recycle, and kill removable files.
Best Practices for Laptops and Mobile Devices
For automated access, personal and technical data, and media files, your laptop and mobile devices would have stored too many saved passwords. It could be a virtual goldmine for attackers if your company has equipped you with a laptop or smartphone for professional use. The cybercriminal may perform unsafe attacks only by hacking or stealing those computers. That is why it is a vital step to carefully hand over your smartphone and laptop.
- If you are using a laptop or handheld computer for doing office work in public areas, consider screen safety.
- If you are not going to use the system in the near future, power it off.
- Enable automatic screen locking after an inactivity time.
- Encrypt all confidential laptop/mobility info.
- Often retain visual or physical control, particularly when going through airport security checkpoints, of your laptop/mobile devices.
- Using public or free Wi-Fi only with the licensed VPN of the company.
- If the computer is missing or stolen, report the failure to the technology department of your protection POC or company immediately.
Tips for Home Computer Security
In general, people do not store information connected to organizations on their home computer/personal computer. These personal computers, however, do have automated authentication facilities for email addresses, social media pages, games, sites of financial institutions, etc. The workers must, however, be aware of how to protect their home computers as well.
Note: These tips are taken from the National Security Agency (NSAPDF )’s “Best Practices to Keep Your Home Network Secure” in the cyber awareness competition.
- For your home machine, do use solid passwords.
- Create different accounts for each user and make them use a powerful password generation process to create their own passwords.
- Download all system security upgrades, patches, antivirus applications, spyware, and firewall, and keep the protections up to date.
- Scan the files periodically for viruses.
- For operating systems and programs, change the default login ID and passwords.
- Back up the files periodically and archive them safely.
Beware of abrupt flickering pop-ups alert that a virus is infected with your computer; this may suggest a malicious attack on the code.
General Security Tips for Online Behavior Outside the Workplace
In their personal time, while employers do not actually monitor what their workers do, they can warn them about the risks of social media and other online channels. The DoD Cyber Awareness Challenge has a chapter that gives tips when browsing online on the best practices.
From this segment of the DoD cyber awareness challenge preparation, here are a few main takeaways:
- Be mindful of the knowledge about yourself and your family that you share publicly.
- It could be used for guessing the passwords, performing doxxing attacks, sending emails for spear/whale phishing, or identity theft.
- Build solid passwords and, if applicable, opt for two-factor (2FA) or multi-factor (MFA) authentication.
- Beware of connections via social networking sites to sports, quizzes, and other applications available. They could contain or exploit you to share your login credentials or other personal information with malicious codes.
- Do not share any classified information on social networking sites about your company, colleagues or clients (no matter what privacy settings you have set on your account).
A Final Word on the DoD Cyber Awareness Challenge
Innovative and advanced ways to perform cyber threats are used by cybercriminals today. People fall for those manipulative tactics, and every year, they lose billions of dollars. Cybersecurity training is, therefore, a must for everyone, particularly for corporate workers and people employed in the technology sector.
As businesses become the victim of a cyber attack because of an employee’s incompetence or insider harassment, they lose not only classified details but also credibility and incur financial damage in court battles. As such, the DoD Cyber Awareness Challenge is a perfect opportunity for organizations to educate their personnel, keep them alert against different forms of cybercriminals, and let them know the best methods of defense. The cyber awareness challenge is a strongly recommended training for all to strengthen every organization’s security posture, regardless of scale.











Leave a Reply